Information systems are constantly changing. Especially if they are functional, production systems, supporting real use. Workstations and servers break. Technology becomes obsolete. New solutions are implemented in response to changing functional requirements.
One thing we don’t know, in the CMMC world, is how much change is too much change.
What is the maximum amount of change allowed?
Between CMMC assessments, we can safely say that unlimited changes for 36 months is the maximum amount of change that the DoD will allow without expiring a CMMC certification.
We can say this because the DoD is already making CMMC certifications expire after 36 months.
What can be changed without triggering a reassessment?
I can’t think of official sources explicitly saying that any changes to the assessed information system are allowable without a re-assessment.
There have been some comments from the DoD that made it sound like changes to the system may trigger re-assessment.
From the CMMC Proposed Rule:
“In rare circumstances a reassessment may be necessary when cybersecurity risks, threats, or awareness have changed.”
What is the historical precedent for smaller changes?
After C3PAOs were assessed against CMMC Level 2 by the DoD, they have been allowed to continue using and changing their information systems without oversight for 36 months. For example, my own company, Kieri Solutions, has been allowed to deploy new workstations to users and make changes to our core solutions without any inquiries by the DoD.
From my perspective, and from talking with a few DIBCAC assessors, it seems like the attitude is:
1) if a company can pass CMMC Level 2, that means they have good knowledge of what is needed for compliance.
2) If a company can pass CMMC Level 2, they also have strong processes and policies to rely upon.
3) Therefore, a company that has passed CMMC Level 2 should be trustworthy to maintain compliance for the three year span.
What is the historical precedent for swapping entire information systems?
I have heard of a few of the Authorized C3PAOs getting special attention by the DoD for performing assessments using systems that were not part of the original assessment – an entirely different information system. For example, some C3PAOs adopted very limited enclaves just to pass a CMMC Level 2 assessment, then found that the enclaves weren’t functional enough to perform work in. At this time, I haven’t heard of any sanctions or repercussions against these C3PAOs, however, it is unlikely that anything would be shared publicly on this topic unless it went to a court case.
This is a fascinating topic to me because the C3PAOs are a sample of what will happen when CMMC is rolled out to a larger group of companies. There absolutely will be defense contractors who get certified on a limited and non-functional information system, with no intention to actually use that information system. I’d hope that they would be found out and subjected to the False Claims Act, but I don’t know.
Related topic: What exactly is “certified” as the result of an assessment?
What does polling of CMMC ecosystem say?
In March 2024, I asked this question to the CMMC Professional community on LinkedIn. Note that most responses were from people working professionally with CMMC. Not necessarily certified assessors.
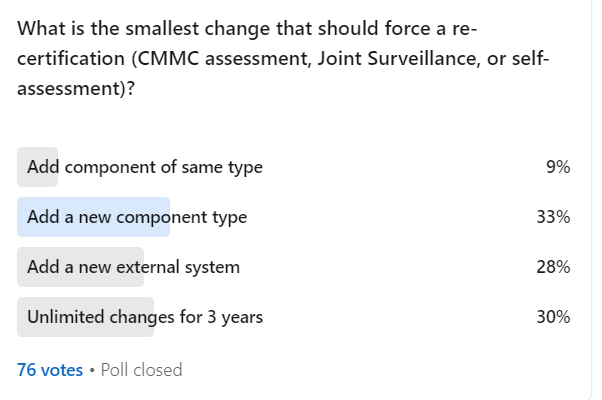
Noteworthy comments and insights from ecosystem members
“Add component of same type” is a wild choice. Federal systems under RMF do not even do that. Adding more of the same / “like-in-kind” / “type accreditation” does not trigger a security relevant change that would require a new assessment. Adding a new component type would likely trigger RMF assessment unless it was a previously assessed enterprise service. Adding an external system interconnection requires a security review but a not new ATO assessment. So, the government answer if following RMF would be B.
Jeff Baldwin, Certified CMMC Assessor
Ultimately, a CMMC assessment should be reviewing the organizational policy and procedures that would include how to add a new component type, what are the gates and reviews involved during that process, and if they don’t have that then they would likely fail the CM requirements in CMMC and not pass the first assessment.
Jeff Baldwin, Certified CMMC Assessor
I voted unlimited changes because… the government has not specified a change notification requirement. Literally, the 32CFR170 and other current regulations are silent on the subject. So although there are such rules in FedRAMP and elsewhere the DoD has not articulated a requirement for something like that to do.
Vincent Scott, Certified CMMC Assessor
When an organization is assessed it should be based on the practices that are in place for any given system, component, facility, person, etc. For example, I have a standard for information system components that list all the security requirements that need to be implemented at a high level. Then I have another document stating how each of those components have implemented that standard or have deviated if needed. The certification process is testing my implementation of the practices or the standard. If I add another component that falls within the same standard then I should not need to obtain another third-party certification.
Terry Hebert, Director IT Security, Centurum
Bottom line – what changes will trigger a CMMC reassessment?
At this time, as long as companies keep using the core information system that was assessed for their certification, and don’t purposefully migrate to an insecure system, the DoD does not seem to hold it against them. From my viewpoint, the 36 month expiration seems to be the only effective trigger for a re-assessment.
However, note the polling results as a key risk factor:
70% of ecosystem members voted for reassessment being required after a significant change, such as adopting a new cloud or adding a new system component type.
How does that popular opinion translate? A typical company would need to be reassessed multiple times a year, unless they purposefully delayed innovation to reduce their change window. Will this lead to close business relationships with C3PAOs, asking them to come in to assess small portions of the information system over time?
For example, a typical medium business may migrate from Windows 10 to Windows 11, change their antivirus provider, and add an email spam filter solution in a single year. Each of these would be an assessable event according to 42% of the respondents.
What about the extreme edge? Any change requires reassessment????
9% of those polled felt that any change to the system, including simply adding more components of the same type, requires re-assessment. An example of this would be adding more users and giving them each a new laptop. I don’t think this is a sustainable path, no matter how motivated the ecosystem is.
We should be able to gather more precedent over 2024 as the first Authorized C3PAOs renew their 3-year CMMC certifications. If we hear about any of them getting in trouble for changes to their system, we will let you know!
Amira Armond is the founder and Quality Manager for Kieri Solutions, an Authorized C3PAO. Kieri Solutions provides CMMC preparation and Authorized C3PAO assessment services. Check their services out at https://www.kieri.com
