At Cloud Security and Compliance Series – CS2 Huntsville, Nick Delrosso’s presentation included the “Top 10 Other Than Satisfied Requirements”.
Nick Delrosso represents the DCMA’s Defense Industrial Base Cybersecurity Assessment Center (DIBCAC) which has been performing cybersecurity assessments on contractors for the last few years.
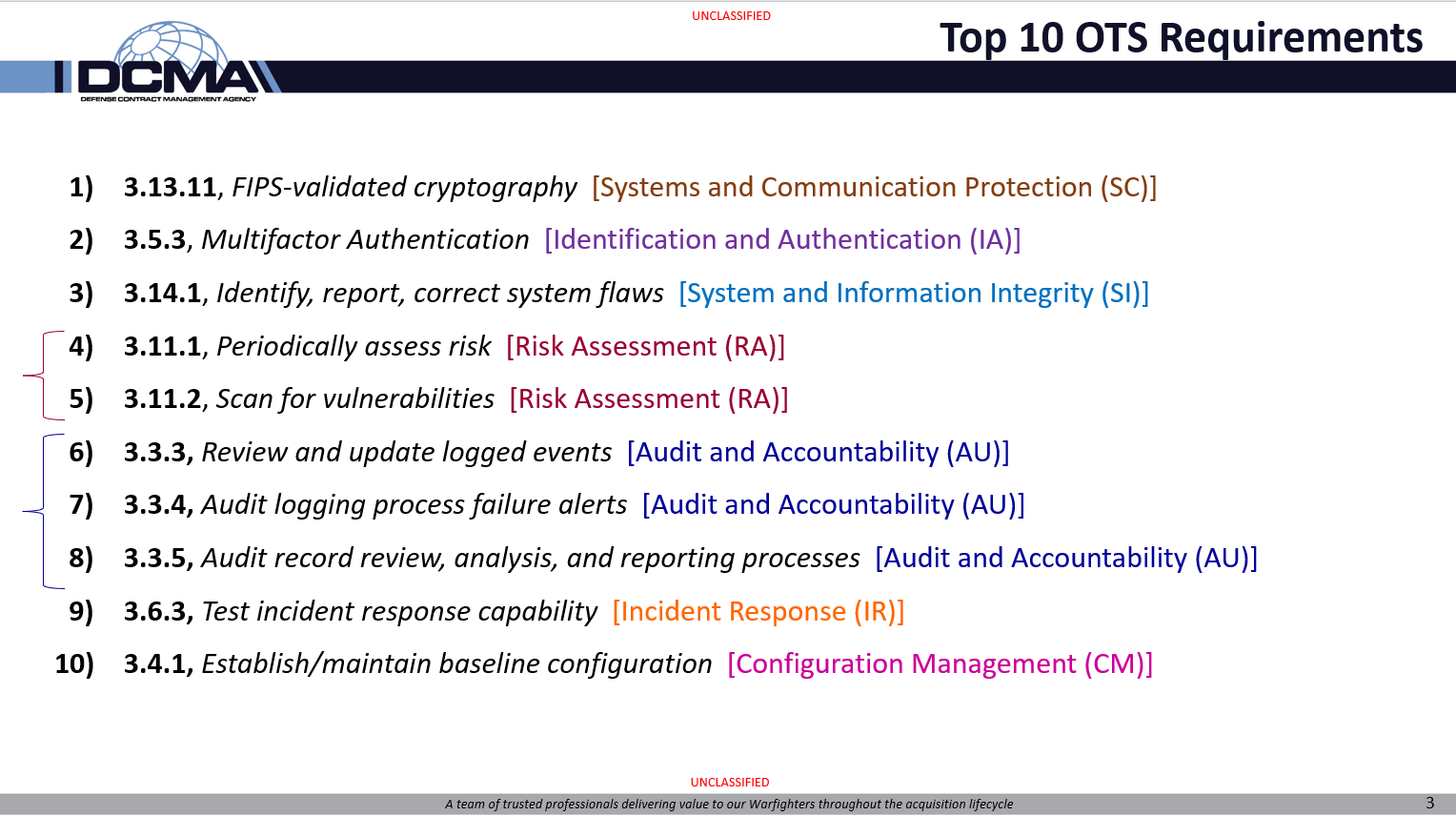
Top 10 failed…
This is the list of the top ten 800-171 security requirements that defense contractors failed to perform, as assessed by DIBCAC.
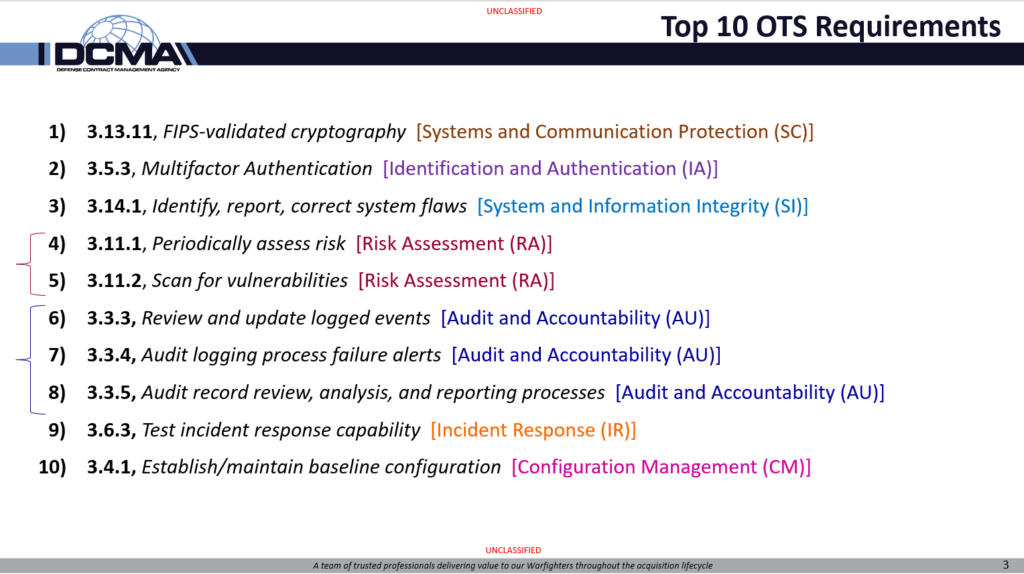
Top 10 misunderstood?
What I noticed is that this list could actually be a “top 10” of MISUNDERSTOOD requirements. For several items, the actual implementation is EASY, just a few hours of work, but most IT professionals don’t understand what is required.
Example: Periodically assess risk. Many IT professionals misunderstand this as either a vulnerability scan or as a security assessment. Totally different things.
For other items, the 800-171 requirement statement itself seems simple, but the assessment adds complexity that defense contractors don’t expect unless they have incorporated 800-171A (the assessment instructions) into their program.
Example: Correct system flaws. The assessment objectives from 800-171A require the contractor to describe deadlines for identifying flaws, deadlines for reporting flaws, and deadlines for correcting flaws. Then the company needs to provide evidence that they performed identification, reporting, and correcting according to those deadlines. Most companies just focus on patching their systems.
Source information from DCMA DIBCAC
This presentation has additional statistics from 117 of DIBCAC’s historical assessments.
Link to presentation from DCMA DIBCAC website
Series to review these failed DIBCAC 800-171 requirements
Over the next few weeks, I will post a mini-series to discuss each of these “Other Than Satisfied” requirements, why companies get them wrong, and how to do better. If you want to see these, make sure to sign up to our newsletter or follow the series on LinkedIn!