On October 15, 2024, the Federal Register was updated with the CMMC Final Rule (32CFR). This rule will be fully effective on December 15, 2024. Link to Federal Register for CMMC This link goes to the U.S. Government’s Federal Register Read More
Tag: 800-171
How to get a CMMC Audit or Assessment
You’re in the right place if the US Government or your prime contractor told you that you need to get a CMMC certification. What is CMMC? CMMC is an initialization for the term “Cybersecurity Maturity Model Certification”. This term was Read More
CMMC JSVA program – what you need to know
Some tidbits about CMMC’s Joint Surveillance Voluntary Assessment (JSVA) program that you might not know: JSVA program is intended to train C3PAOs and CMMC Assessors 1) The DoD is essentially using the JSVA program to train and vet our private Read More
How to submit a NIST SP 800-171 self assessment to SPRS
Answers to common questions about how to submit your NIST SP 800-171 self assessment to SPRS. Register an account, how to handle multiple…
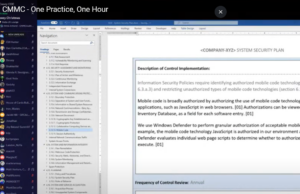
How the secret sauce is made – one practice, one hour
How does a defense contractor create a plan to perform each requirement in CMMC and NIST SP 800-171? Will you fail if you don’t write policy statements which regurgitate each requirement in a ‘shall” form? AKA “𝘚𝘢𝘧𝘦𝘨𝘶𝘢𝘳𝘥𝘪𝘯𝘨 𝘮𝘦𝘢𝘴𝘶𝘳𝘦𝘴 𝘧𝘰𝘳 𝘊𝘜𝘐 Read More
CMMC Breaking News – July 25, 2023
Today we had two big events in #CMMC and US Federal Contractor Cybersecurity. The Rule for CMMC moved to the Office of Management and Budget. That means a timer has started, 90 days or less, for the review to complete. Expect the Read More
3.13.11 FIPS 140-2 Validated Cryptography
It is time, finally, to talk about the #1 “Other than Satisfied” requirement in 800-171, per historic DIBCAC assessments. 😱 💥 💥 𝐅𝐈𝐏𝐒 140-2 𝐕𝐚𝐥𝐢𝐝𝐚𝐭𝐞𝐝 𝐌𝐨𝐝𝐮𝐥𝐞𝐬 💥 💥 😱 Listen up – I’m going to tell you how to succeed Read More
3.5.3 Multifactor Authentication
Multifactor Authentication: #2 of the top 10 “Other than Satisfied Requirements” for 800-171 assessments by DIBCAC. 𝐔𝐬𝐞 𝐦𝐮𝐥𝐭𝐢𝐟𝐚𝐜𝐭𝐨𝐫 𝐚𝐮𝐭𝐡𝐞𝐧𝐭𝐢𝐜𝐚𝐭𝐢𝐨𝐧 𝐟𝐨𝐫 𝐥𝐨𝐜𝐚𝐥 𝐚𝐧𝐝 𝐧𝐞𝐭𝐰𝐨𝐫𝐤 𝐚𝐜𝐜𝐞𝐬𝐬 𝐭𝐨 𝐩𝐫𝐢𝐯𝐢𝐥𝐞𝐠𝐞𝐝 𝐚𝐜𝐜𝐨𝐮𝐧𝐭𝐬 𝐚𝐧𝐝 𝐟𝐨𝐫 𝐧𝐞𝐭𝐰𝐨𝐫𝐤 𝐚𝐜𝐜𝐞𝐬𝐬 𝐭𝐨 𝐧𝐨𝐧-𝐩𝐫𝐢𝐯𝐢𝐥𝐞𝐠𝐞𝐝 𝐚𝐜𝐜𝐨𝐮𝐧𝐭𝐬. My theory is that most of Read More
What are Spot Checks for?
𝐂𝐌𝐌𝐂 𝐀𝐬𝐬𝐞𝐬𝐬𝐦𝐞𝐧𝐭 𝐒𝐩𝐨𝐭 𝐂𝐡𝐞𝐜𝐤𝐬 “𝘐𝘧 𝘤𝘰𝘯𝘵𝘳𝘢𝘤𝘵𝘰𝘳’𝘴 𝘳𝘪𝘴𝘬-𝘣𝘢𝘴𝘦𝘥 𝘴𝘦𝘤𝘶𝘳𝘪𝘵𝘺 𝘱𝘰𝘭𝘪𝘤𝘪𝘦𝘴, 𝘱𝘳𝘰𝘤𝘦𝘥𝘶𝘳𝘦𝘴, 𝘢𝘯𝘥 𝘱𝘳𝘢𝘤𝘵𝘪𝘤𝘦𝘴 𝘥𝘰𝘤𝘶𝘮𝘦𝘯𝘵𝘢𝘵𝘪𝘰𝘯 𝘰𝘳 𝘰𝘵𝘩𝘦𝘳 𝘧𝘪𝘯𝘥𝘪𝘯𝘨𝘴 𝘳𝘢𝘪𝘴𝘦 𝘲𝘶𝘦𝘴𝘵𝘪𝘰𝘯𝘴 𝘢𝘣𝘰𝘶𝘵 𝘵𝘩𝘦𝘴𝘦 𝘢𝘴𝘴𝘦𝘵𝘴, 𝘵𝘩𝘦 𝘢𝘴𝘴𝘦𝘴𝘴𝘰𝘳 𝘤𝘢𝘯 𝘤𝘰𝘯𝘥𝘶𝘤𝘵 𝘢 𝘭𝘪𝘮𝘪𝘵𝘦𝘥 𝘴𝘱𝘰𝘵 𝘤𝘩𝘦𝘤𝘬 𝘵𝘰 𝘪𝘥𝘦𝘯𝘵𝘪𝘧𝘺 𝘳𝘪𝘴𝘬𝘴. 𝘛𝘩𝘦 𝘭𝘪𝘮𝘪𝘵𝘦𝘥 𝘴𝘱𝘰𝘵 𝘤𝘩𝘦𝘤𝘬(𝘴) 𝘴𝘩𝘢𝘭𝘭 𝘯𝘰𝘵 𝘮𝘢𝘵𝘦𝘳𝘪𝘢𝘭𝘭𝘺 𝘪𝘯𝘤𝘳𝘦𝘢𝘴𝘦 𝘵𝘩𝘦 Read More
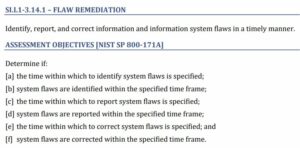
3.14.1 Identify, report, correct system flaws
Continuing the Top 10 “Other than Satisfied Requirements” for 800-171 assessments by DIBCAC. “𝐈𝐝𝐞𝐧𝐭𝐢𝐟𝐲, 𝐫𝐞𝐩𝐨𝐫𝐭, 𝐚𝐧𝐝 𝐜𝐨𝐫𝐫𝐞𝐜𝐭 𝐢𝐧𝐟𝐨𝐫𝐦𝐚𝐭𝐢𝐨𝐧 𝐚𝐧𝐝 𝐢𝐧𝐟𝐨𝐫𝐦𝐚𝐭𝐢𝐨𝐧 𝐬𝐲𝐬𝐭𝐞𝐦 𝐟𝐥𝐚𝐰𝐬 𝐢𝐧 𝐚 𝐭𝐢𝐦𝐞𝐥𝐲 𝐦𝐚𝐧𝐧𝐞𝐫.” This is the third most “Other than Satisfied” requirement. 3.14.1 is both misunderstood and Read More
3.11.1 Periodically assess the risk to organizational operations
3.11.1 𝐏𝐞𝐫𝐢𝐨𝐝𝐢𝐜𝐚𝐥𝐥𝐲 𝐚𝐬𝐬𝐞𝐬𝐬 𝐫𝐢𝐬𝐤…This is the fourth-most “Other than satisfied” #CMMC requirement. Periodically assess the risk to organizational operations (including mission, functions, image, or reputation), organizational assets, and individuals, resulting from the operation of organizational systems and the associated processing, storage, or Read More
3.11.2 Scan for Vulnerabilities
Scan for vulnerabilities….This the fifth-most “Other than satisfied” #CMMC requirement with an 18% fail rate. 3.11.2 𝐒𝐜𝐚𝐧 𝐟𝐨𝐫 𝐯𝐮𝐥𝐧𝐞𝐫𝐚𝐛𝐢𝐥𝐢𝐭𝐢𝐞𝐬 𝐢𝐧 𝐨𝐫𝐠𝐚𝐧𝐢𝐳𝐚𝐭𝐢𝐨𝐧𝐚𝐥 𝐬𝐲𝐬𝐭𝐞𝐦𝐬 𝐚𝐧𝐝 𝐚𝐩𝐩𝐥𝐢𝐜𝐚𝐭𝐢𝐨𝐧𝐬 𝐩𝐞𝐫𝐢𝐨𝐝𝐢𝐜𝐚𝐥𝐥𝐲 𝐚𝐧𝐝 𝐰𝐡𝐞𝐧 𝐧𝐞𝐰 𝐯𝐮𝐥𝐧𝐞𝐫𝐚𝐛𝐢𝐥𝐢𝐭𝐢𝐞𝐬 𝐚𝐟𝐟𝐞𝐜𝐭𝐢𝐧𝐠 𝐭𝐡𝐨𝐬𝐞 𝐬𝐲𝐬𝐭𝐞𝐦𝐬 𝐚𝐧𝐝 𝐚𝐩𝐩𝐥𝐢𝐜𝐚𝐭𝐢𝐨𝐧𝐬 𝐚𝐫𝐞 𝐢𝐝𝐞𝐧𝐭𝐢𝐟𝐢𝐞𝐝. “𝒐𝒓𝒈𝒂𝒏𝒊𝒛𝒂𝒕𝒊𝒐𝒏𝒂𝒍 𝒔𝒚𝒔𝒕𝒆𝒎𝒔”…This is an example of Read More
3.3.3 Review and Update Logged Events
This is #6 in the series of most common failed requirements as assessed by the DoD’s Cyber Assessment Center. This requirement is another example of misunderstanding == failing (alongside the other top 10 requirements). Most people do not understand what Read More
3.3.4 Audit Logging Process Failure
Continuing the Top 10 Failed Requirements for 800-171! Onward to #7: 3.3.4 “𝐀𝐥𝐞𝐫𝐭 𝐢𝐧 𝐭𝐡𝐞 𝐞𝐯𝐞𝐧𝐭 𝐨𝐟 𝐚𝐧 𝐚𝐮𝐝𝐢𝐭 𝐥𝐨𝐠𝐠𝐢𝐧𝐠 𝐩𝐫𝐨𝐜𝐞𝐬𝐬 𝐟𝐚𝐢𝐥𝐮𝐫𝐞.” Sit with me while I tell a story… 𝘈𝘯 𝘰𝘳𝘨𝘢𝘯𝘪𝘻𝘢𝘵𝘪𝘰𝘯 𝘥𝘪𝘴𝘤𝘰𝘷𝘦𝘳𝘴 𝘵𝘩𝘢𝘵 𝘵𝘩𝘦𝘺 𝘸𝘦𝘳𝘦 𝘣𝘳𝘦𝘢𝘤𝘩𝘦𝘥 𝘣𝘦𝘤𝘢𝘶𝘴𝘦 𝘨𝘰𝘷𝘦𝘳𝘯𝘮𝘦𝘯𝘵 𝘴𝘦𝘤𝘳𝘦𝘵𝘴 Read More
3.3.5 Correlate Audit Processes
NIST SP 800-171 3.3.5 𝐂𝐨𝐫𝐫𝐞𝐥𝐚𝐭𝐞 𝐚𝐮𝐝𝐢𝐭 𝐫𝐞𝐜𝐨𝐫𝐝 𝐫𝐞𝐯𝐢𝐞𝐰, 𝐚𝐧𝐚𝐥𝐲𝐬𝐢𝐬, 𝐚𝐧𝐝 𝐫𝐞𝐩𝐨𝐫𝐭𝐢𝐧𝐠 𝐩𝐫𝐨𝐜𝐞𝐬𝐬𝐞𝐬 𝐟𝐨𝐫 𝐢𝐧𝐯𝐞𝐬𝐭𝐢𝐠𝐚𝐭𝐢𝐨𝐧 𝐚𝐧𝐝 𝐫𝐞𝐬𝐩𝐨𝐧𝐬𝐞 𝐭𝐨 𝐢𝐧𝐝𝐢𝐜𝐚𝐭𝐢𝐨𝐧𝐬 𝐨𝐟 𝐮𝐧𝐥𝐚𝐰𝐟𝐮𝐥, 𝐮𝐧𝐚𝐮𝐭𝐡𝐨𝐫𝐢𝐳𝐞𝐝, 𝐬𝐮𝐬𝐩𝐢𝐜𝐢𝐨𝐮𝐬, 𝐨𝐫 𝐮𝐧𝐮𝐬𝐮𝐚𝐥 𝐚𝐜𝐭𝐢𝐯𝐢𝐭𝐲. This is the 8th most likely requirement to be “other than satisfied” by defense contractors, according Read More
3.6.3 Test the Organizational Incident Response Capability
This was originally posted on LinkedIn. Check the original post and community discussion here! On to the next requirement! 3.6.3 𝐓𝐞𝐬𝐭 𝐭𝐡𝐞 𝐨𝐫𝐠𝐚𝐧𝐢𝐳𝐚𝐭𝐢𝐨𝐧𝐚𝐥 𝐢𝐧𝐜𝐢𝐝𝐞𝐧𝐭 𝐫𝐞𝐬𝐩𝐨𝐧𝐬𝐞 𝐜𝐚𝐩𝐚𝐛𝐢𝐥𝐢𝐭𝐲. This is post #5 in my series analyzing the top ten failed / misunderstood Read More
3.4.1 Establish / Maintain Baseline Configurations
This series reviews the top failed (misunderstood) 800-171 and CMMC requirements. Originally posted on LinkedIn – check the start of series here for community conversation and thoughts! 3.4.1 𝐄𝐬𝐭𝐚𝐛𝐥𝐢𝐬𝐡/𝐦𝐚𝐢𝐧𝐭𝐚𝐢𝐧 𝐛𝐚𝐬𝐞𝐥𝐢𝐧𝐞 𝐜𝐨𝐧𝐟𝐢𝐠𝐮𝐫𝐚𝐭𝐢𝐨𝐧𝐬 This one is both commonly misunderstood and difficult to implement, even though Read More
Excuses that won’t work for your CMMC assessment
Public Safety Announcement for #CMMC and DIBCAC assessments of 800-171 compliance. “My _________ is scheduled to occur in January and we haven’t reached January yet.” – said too many Organizations Seeking Certification Do not try to use this excuse to explain why Read More
Top 10 “Other than satisfied” 800-171 requirements
At Cloud Security and Compliance Series – CS2 Huntsville, Nick Delrosso’s presentation included the “Top 10 Other Than Satisfied Requirements”. Nick Delrosso represents the DCMA’s Defense Industrial Base Cybersecurity Assessment Center (DIBCAC) which has been performing cybersecurity assessments on contractors for the Read More
When is a FIPS Validated Module required?
This video from Amira Armond and Jillian Wright (both Kieri Solutions Provisional Assessors and Instructors), explains when FIPS 140-2 validated modules are required to be used by CMMC Level 2 / NIST SP 800-171. It also explains when FIPS is Read More
Lessons learned from two (three?) DIBCAC assessments
On behalf of CMMCAudit.org, I’m excited to share this interview with Jake Williams about his lessons learned from two DIBCAC assessments of DFARS 252.204-7012 and NIST SP 800-171 compliance. This video is packed with actionable information about what to expect during assessments. Read More
Defining authorized – a key concept in CMMC
The term authorized is used across 40 different assessment objectives in the CMMC. Do you know what it means? How do you show it?
Conversations from LinkedIn
This page is an index of LinkedIn discussions and posts about CMMC and 800-171. It will be updated over time with new topics.
CMMC RM.2.142 Scan for vulnerabilities in organizational systems
This article is an in-depth review of the CMMC Level 2 Requirement RM.2.142 on the topic of vulnerability scanning. I break out frequently asked questions and reference other requirements that are related to vulnerability scanning. This requirement also applies to current DFARS 252.204-7012 and NIST SP 800-171 organizations that hold CUI
DFARS 252.204-7012 or 252.204-7021 enforces NIST 800-171 and CMMC
If you are a Defense Contractor that handles Controlled Unclassified Information (CUI), this news is going to be very important for you. DFARS 252.204-7012 Interim Rule Yesterday, the DoD released an interim rule to the Defense Federal Acquisition Rules Supplement Read More
Remote Management & Access Tools for 800-171 and CMMC
A question came up today from a client that has a large remote workforce. “How can my help desk manage end user devices while staying compliant with 800-171 and CMMC?” For example, can we use remote access tools like LogMeIn Read More