Are you using a Managed Service Provider for your CMMC-compliant information system? Are you a Managed Service Provider with defense contractor clients? This article discusses the risks and pitfalls of having an MSP “in-scope” during your CMMC assessment, and gives tips for a better experience.
This article is provided by our sponsor, Kieri Solutions, an authorized CMMC Third Party Assessment Organization (C3PAO). Kieri Solutions provides assessment services, high-quality CMMC consulting, and an easy to use compliance documentation package geared toward small and medium businesses.
MSPs add wildcard risk to your CMMC assessment
Your MSP will be in-scope for your assessment. At the least, their staff are relied upon to perform security procedures such as patching and account management. In worst-case scenarios, MSPs link their network directly to client networks without strong boundary protections, allowing their insecure computers to create openings for client network compromise.
Your MSP must be willing to do the hard work of CMMC compliance every day. They have to perform formal change management procedures. They have to enforce multi-factor authentication and complex passwords on their own accounts. They need to perform maintenance and escalate to fix systems that fail to patch. All these activities need to come with evidence – the MSP needs to take careful notes or follow procedures that generate records.
The scary thing is, the vast majority of commercially-focused MSPs do not operate in a security mindset. They want to use simple passwords, and if you force them to use complex passwords, they will choose something like “Pa$$w0rd1!”. They don’t want to spend the extra time to do change management or to track baseline configurations. They look for outsourced solutions that have the best monthly profit ratio, rather than ensuring those vendors can be trusted with CUI. It is extremely hard to change a culture that disregards security. It is unlikely that you as a client will be able to change your MSP’s culture. The lower risk option is to pick an MSP that is already security oriented and has several defense contractors as clients.
Choosing the wrong Managed Service Provider will directly affect your ability to comply with CMMC and pass an assessment.
Kieri Solution’s MSP story
As an CMMC Third Party Assessment Organization (C3PAO) candidate, one of the tests to become authorized was passing a CMMC assessment of our own information system. At that time, our company was very small – just like the smallest of defense contractors. If you are a 1-3 person contractor facing CMMC, we are very sympathetic because we went through it ourselves!
When we considered how to build this CMMC compliant information system, we considered outsourcing the work to a MSP. We had defense contractor clients who hired integrators and MSPs so we were able to observe the process.
– One client had hired an RPO integrator to migrate them to Microsoft GCC-High for CMMC Level 3 (now level 2) compliance, prior to engaging us. The integrator charged upwards of $80,000 and essentially did a data migration + onboarding scripts to the new tenant for their laptops. Zero security policies were applied to the laptops. Event logging wasn’t turned on. Accounts and users still had out-of-control permissions. The integrator didn’t provide details needed for the system security plan. When we started asking questions mid-project, it became clear that they were just doing a commercial-level migration and had no special techniques for CMMC. It took our client an extra 6 months to resolve this mess.
– Several clients had Managed Service Providers to support their 100-300 user networks. Some of the Managed Service Providers actually did have incident management-dedicated staff, but none had someone with Governance Risk and Compliance (GRC) skillset – an essential cybersecurity skillset for compliance with CMMC. The MSPs were invariably using third party cloud-based management tools that didn’t have security certifications. Technically, the tools were expected to be secured at CMMC levels (which is/was impossible because CMMC assessments aren’t available for MSP tools) but they also didn’t have any other security assessment done that we could use as proof that the tools were being managed securely.
– At that time (2020), none of the MSPs and integrators we knew about were doing the manual procedures of compliance reliably: change management, account management, applying recommended secure configuration settings, capturing baselines. Since then, a few MSPs have shown that they understand what is necessary for CMMC compliance, but at the time, we had not seen any successes.
Ultimately, we decided that outsourcing our compliance to an MSP was too dangerous and developed our own program for compliance. This program included simple but repeatable procedures, policy, and checklists designed for a small business to perform CMMC efficiently. We figured out how to build a very secure network that was still functional for everyday work. We wrote an extremely detailed and high-quality system security plan and gathered proof of FIPS 140-2 encryption for all data flows. And we passed our CMMC assessment to become the 13th Authorized C3PAO.
But figuring it all out from scratch was extremely expensive – we estimate that we spent over 1500 hours of senior cybersecurity and system engineering labor to build the system and create all the compliance documentation. (And lots of revisions with lessons learned and making everything more streamlined and efficient). Our investment is paying off, we are in high demand as a result, but we definitely have sympathy for the small defense contractor who is calculating their return on investment!
Why use an MSP if they are risky?
For small businesses, the cost of hiring a few competent IT people (necessary to create and operate a CMMC compliant network) is way out of budget. By using an MSP, you can leverage economies of scale that simply don’t exist if you try to do it yourself.
First, a good MSP will have procedures to build secure networks. This experience saves time and missteps, reducing cost dramatically.
Secondly, a good MSP will have fractional staff available with the right skills. Ideally, all defense contractors will have access to senior cybersecurity experts, senior system engineers, a dedicated maintenance and patching team, a dedicated incident response team, and a 24×7 helpdesk. That is unaffordable for a small business with 30 employees. But an MSP supporting multiple businesses can provide this level of experience.
If you can find a good MSP and have an efficient set of policies and procedures, you can skip the 1500+ hours of senior-level work to build it from scratch. It will still be alarmingly expensive (CMMC compliance is expensive!), but not as much as if you try to figure it out yourself.
Applicable CMMC practices for MSPs
People
Expect that training, privileged management, and account requirements will be applicable to your MSP’s staff.
Your MSP should have internal programs to do the following: identify which staff are authorized to access your network; perform background screening; limit the privileged roles that their staff are granted; uniquely identify any individuals accessing your system; perform special cybersecurity and role-based training for their staff; and promptly remove their access if they leave the company.
Technology
A typical MSP will use third party cloud services for remote management of their client’s computers. This is the #1 way that MSP technology becomes “in-scope” for CMMC.
There is an entire industry of third party cloud services designed for MSPs to use. These cloud services let MSPs access and manage multiple clients from a central console. This can be a big problem if you are trying to be compliant with CMMC, because CMMC expects you to prove to an assessor that these cloud services are highly secure. Proof is often unavailable for these MSP cloud services.
By deploying agents to a defense contractor’s network, the MSP establishes persistent access to the network. That means that if the remote management cloud is compromised, the defense contractor can be compromised too, using that persistent access.
The diagram below shows how a typical MSP uses cloud services to manage their clients.
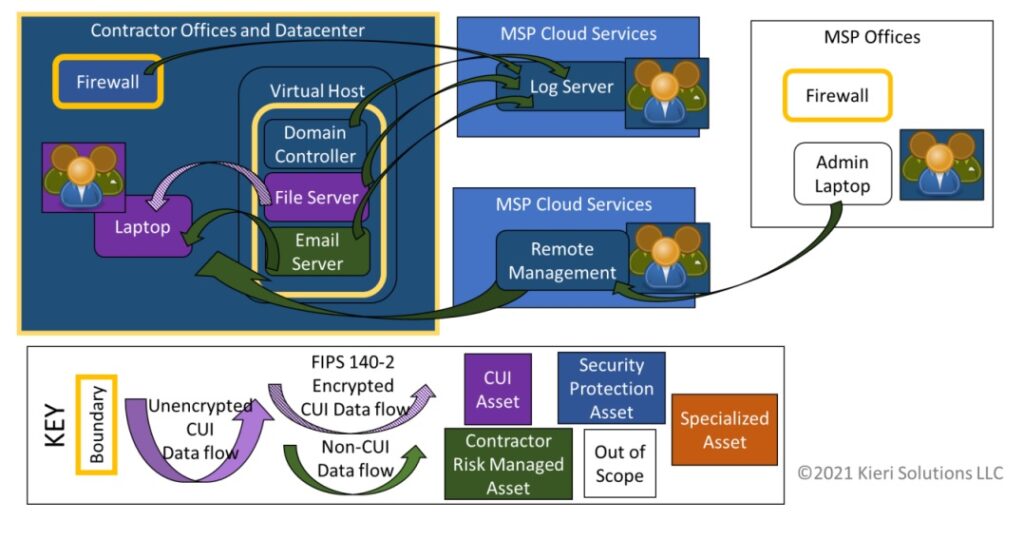
Scenario 11 from the CMMC Scoping Scenarios Analysis paper
Facilities
It is unlikely that an MSP’s facilities will have any applicable practices during your assessment. Most MSPs that use third party cloud-based management tools should not have their facilities in-scope.
What are good and bad reasons for an MSP’s facilities to be in-scope?
Good reason – the MSP self-hosts management servers in their facility because they don’t trust third-party cloud-based management tools. The datacenter protecting the servers may have applicable practices.
Bad reason – the MSP has established a permanent network connection to your network and anyone in their facility could plug in a laptop and access your network. The MSP facility needs to be protected because it is an essential defense for your data.
Bad reason – the MSP has moved Controlled Unclassified Information into their servers or has saved data from one of your computers to an external hard drive. This is typically done as a backup or possibly as part of doing a migration. Now the MSP facility needs to be protected because there is CUI at their facility.
Tips for CMMC success with an MSP
Choose your MSP carefully
MSP Risk System Questionnaire (Excel)
Allison Giddens, one of the leading advocates for small defense contractors, created an MSP scoring questionnaire to use while interviewing MSPs. Credit to Allison Giddens and the Cooey Center of Excellence.
This Risk System provides standard questions to ask your MSP, such as “Are you willing to add me to your cyber insurance?”, “Are all people working for your company U.S. persons?”, and “Is MFA enforced for administrator access?”. Based on the answers, it generates a risk score and recommends whether the MSP is a good candidate for supporting defense contractors.
Please note that this questionnaire was made by Allison Giddens, with input from the Discord Cooey Center of Excellence community. Permission to re-publish was provided by Allison Giddens.
Demand a Shared Responsibility Matrix (or Customer Responsibility Matrix)
You will need to identify exactly what the MSP does for your organization at an Assessment Objective (AO) level. At this time, it is very rare to find MSPs that have a Shared Responsibility Matrix for CMMC ready. You may have to demand that they create one for you.
The C3PAO Stakeholder Forum hosts a free (no registration needed) Shared Responsibility Matrix template that can be used:
Shared Responsibility Matrix (Word)
The Shared Responsibility Matrix should accurately describe which organization is responsible for each Assessment Objective. Any shared responsibilities should be listed. For example, an MSP may be responsible for “controlling connection of mobile devices” but a typical contractor will have a shared responsibility to educate their users and follow procedures for BYOD use.
Keep FedRAMP requirements where they should be
The Department of Defense seems poised to require FedRAMP authorization “or equivalent” from any MSP that stores, processes, or transmits CUI.
What is FedRAMP and why are we talking about it?
FedRAMP is a cybersecurity framework designed for large, automated, self-service cloud providers like AWS and Microsoft 365. FedRAMP moderate has 325 controls which include availability, integrity, and confidentiality. FedRAMP requires roughly three times more security controls than CMMC Level 2 does.
It is unreasonable to expect MSPs to perform FedRAMP controls for their information system. The cost of performing FedRAMP is often more than 2 million dollars and requires several full-time cybersecurity staff just to maintain a strictly virtual system, let alone a traditional information system with regular users, printers, and computers. Once FedRAMP controls are fully implemented, the cost of continuing compliance (labor, security systems) is often around $500,000 per year. MSPs simply don’t have the revenue to pay for this.
Defense contractors are only required to do CMMC requirements (about 110 requirements focused on confidentiality) to protect Controlled Unclassified Information. Defense contractors can share CUI with their partners and subcontractors who are also only required to do CMMC requirements.
Unfortunately, the second that you share CUI with an MSP, the MSP will be required to comply with FedRAMP. That means that the same data now needs to be protected at 3x the requirements and more than 3x the cost. Ironically in this situation, FedRAMP would apply to organizations dedicated to supporting the smallest and most vulnerable defense contractors, but it doesn’t apply to huge defense contractors that have much more Controlled Unclassified Information than any MSP would ever encounter. The irony of this situation appears to be lost on the DoD.
What is the problem with requiring FedRAMP for MSPs?
If MSPs are forced to attest they are FedRAMP or FedRAMP “equivalent” to support their small defense contractor clients, I believe they will either falsify their documentation (self-attestation!) or stop supporting defense contractors. Neither option improves security for defense contractors.
Think I’m being ridiculous? FedRAMP “equivalent” requires multiple datacenters that can instantly fail over in case of disaster. It requires use of smart cards for logons instead of passwords. It requires temporary accounts to be automatically disabled over time. It requires third party penetration testing. It requires several full-time cybersecurity staff to maintain. These are special capabilities that would be very very expensive to implement for most MSP networks.
FedRAMP “equivalent” requires all the same security and technology that FedRAMP “authorized” does. It has the same requirements. It has the same expectations. The only real difference is that authorized means a government agency has reviewed your third-party FedRAMP assessment and declared that your cloud can be used by the Federal government.
Some people think that “FedRAMP equivalent” means “no security required”. That is wrong!! The DoD appears to be on-track to force a real assessment of FedRAMP equivalent to verify that all the controls required by FedRAMP are actually performed by your service providers.
Every single MSP I’ve talked to, even ones that have experience with FedRAMP, has said that it is insane to require an MSP to do all the FedRAMP requirements for their internal laptops and support staff. FedRAMP is designed for large multi-tenant cloud systems which have strictly controlled boundaries (no laptops in scope, no regular users in scope).
How to prevent your MSP from being forced to lie or stop supporting you
In order to make it obvious that FedRAMP requirements don’t apply to your MSP, follow these architectural guidelines:
-If you use [real] cloud services to store or process CUI, always purchase your own subscription and issue accounts to your MSP’s staff. Never let the MSP host your data using their cloud subscriptions.
-Have a signed agreement (memorandum of understanding, contract, service agreement) that states the MSP will never download data files from your environment, even to investigate cyber incidents. Have them articulate how they will perform this task internally. The MSP should train their employees and configure their remote management systems to prevent file download.
-Never store backups at the MSP or use the MSP for co-location failover services. Instead, use defense contractor partners or subcontractors or leased facilities for this.
Keep insecure MSP technology out of scope
If you aren’t sure that your MSP is operating their own information system and technology securely, keep it out of scope. Follow these guidelines to reduce MSP scope to just their people (then argue that the people are inside YOUR scope of assessment, not the MSP’s scope):
-Identify a few MSP staff who are allowed to work on your network. Identify them by name and issue them individual privileged accounts to your system. Have a formal agreement with the MSP that only these identified staff will support your network and they will NOT share their passwords with other MSP personnel.
-Install your own management servers (such as log servers, antivirus servers, patching) inside your network. Don’t use the MSP’s servers. This ensures that unauthorized people at the MSP, or if it is a third party cloud-based management system, the administrators of the cloud, cannot access your systems.
-Don’t let the MSP establish VPN sessions into your network using their own laptops. Connecting MSP laptops inside your network boundaries means that their laptops become in-scope (this is bad if those laptops aren’t very secure). Instead, issue the MSP your own secure laptops to use when managing your environment.
Allow secure MSP technology in-scope
I only recommend keeping your MSP’s technology out of scope if you can’t trust it to be secure. If the MSP is allowed to use their technology stack to support you, they will be happier and compliance will cost less than if they have to use your network for everything.
Some of the best defense-focused MSPs operate their own management servers. By operating their own servers (rather than outsourcing this to a third party cloud with no visibility), the MSP can ensure that only authorized people have access to client networks.
If your MSP’s technology is in-scope, you should plan for their network to be CMMC assessed. Most assessors will not want to assess two totally separate networks (your network and your MSP’s network) at the same time. Ideally, your MSP will coordinate with a CMMC assessor to have their network assessed against CMMC Level 2 first. Then you will know that their network is secure and that you only have to worry about your own network’s compliance.
Engage your MSP to help during assessment
If your MSP is performing system management and maintenance on your behalf, you will need them to participate in your assessment to describe what they do.
A top-notch MSP will provide a system security plan as part of their service offering. If the MSP says that they are responsible for a practice, they should provide the system security plan description for that requirement. This is a huge way that MSPs can make life easier on their clients, since only the MSP actually knows the intricate details of the network and how they perform cybersecurity.
Have a conversation about CMMC before starting
The last piece of advice I will leave you with is to have a detailed conversation with your MSP before starting a CMMC compliance project.
If you just say “I need to be compliant with CMMC Level 2 at the end of this project”, it is highly likely that you will be disappointed toward the end of the project. Sales staff are going to say yes without understanding the level of effort involved.
If you don’t have a senior cybersecurity person on staff (if you are considering getting an MSP, you probably don’t), it is a really good idea to hire a consultant who knows what is necessary for CMMC compliance. Allocate them 10 hours to help you interview, choose an MSP, and have meetings to ensure that the MSP fully understands expectations for how to build and run your network. If you choose an MSP who does not have CMMC experts on staff, consider keeping your consultant as a virtual CISO to oversee the MSP’s work at least monthly.
What other advice and tips would you give?
Do you disagree with anything said in this article?
If you were advising an MSP on how to serve their defense contractor clients, how would your advice change?
Would love to hear your thoughts in the comments below!
This article is provided by our sponsor, Kieri Solutions, an authorized CMMC Third Party Assessment Organization (C3PAO). Kieri Solutions provides assessment services, high-quality CMMC consulting, and an easy to use compliance documentation package geared toward small and medium businesses.
If you would like a demo of Kieri’s documentation package, would like to get on-schedule for a CMMC assessment, or need some consulting support from proven experts, reach out! info@kieri.com
Don’t forget to sign up for our newsletter and connect with Amira Armond on LinkedIn for CMMC news and the latest articles.

Shouldn’t “This Risk System provides standard questions to ask your MSP, such as “Are you willing to add me to your cyber insurance?”, “Are all people working for your company U.S. citizens?” ” be U.S. persons?
Great comment Robert. Changed to “US Persons”, though I believe the questionnaire still says “US Citizens” inside it.
US Citizen is generally only appropriate if everyone on the contract is expected to have a clearance.