This page describes how to find the CMMC requirements, how to interpret them, and how to start preparing for an outside audit.
It explains how to read the CMMC document and how your team or an auditor would check each requirement against your information systems.
Disclaimer: The goal is to help you understand how the CMMC is organized and numbered. I might have some things wrong and the CMMC will definitely change over time. Please comment below to give guidance that is missing here!
I recommend reading through this CMMC glossary of terms and definitions. It is a “who’s who” and “what’s what” for the entire CMMC and DoD cybersecurity infrastructure.
Link to Official CMMC Model page: https://www.acq.osd.mil/cmmc/draft.html
Update January 4, 2021: According to the DoD’s latest information, the only authoritative documents in this location for the CMMC are the “CMMC Model v1.02” and the CMMC Level 1 / 3 Assessment Guides. The CMMC Model Appendices are out of date.
The CMMC Level 3 Assessment Guide has a detailed description of each security requirement. This is an excellent resource because it gives examples of how organizations secure their networks for each security requirement.
What is a cybersecurity control?
Quick definition: In the cybersecurity industry, the word “control” is used to refer to a single security requirement or activity to reduce risk.
Experienced cybersecurity professionals who have been working with other frameworks (such as NIST SP 800-53) tend to want to add related controls for CMMC assessment and implementation. This is not appropriate for CMMC. The CMMC doesn’t mention the word “control” and there are additional implications for controls (based on other security frameworks) which are not relevant for CMMC.
The CMMC calls its single security requirements “practices” (short for best practices). When referencing CMMC requirements, the best term to use is “practice” for an individual requirement. It is also appropriate to use the word “requirement”.
How do I prepare for the CMMC?
1. Gather CMMC documents, templates, and tools
Download the latest version of the CMMC here (download the Assessment Guide (for Level 1 or 3, depending on your company))
Review this article for recommended templates and assessment tools
2. Identify the scope of your evaluation
So far, CMMC sounds like it will measure scope very similarly to how NIST SP 800-171 is performed, except for a wider range of sensitive information.
Every defense contractor with a contract will have Federal Contract Information (FCI) at least. This term is used in CMMC Level 1 and 2 and seems to define the information it is trying to protect. So any organizational system that processes or stores or is able to contact FCI would be in scope for a level 1 or 2 audit.
For example, if your email server has FCI in it because the government has sent you emails, then your scope includes…
- any other server that is on the same network as your email server
- admin workstations that manage the email server
- user workstations that get emails from the email server
- mobile phones that get emails from the email server
- the backup server
- and so forth
For level 1, I would expect most small and medium defense contractors to audit their entire network because it is easier to do that then segment out everyday communications from the government. Note: larger companies that haven’t prioritized cybersecurity in the past may find it too hard to reach level 1 across their entire enterprise, and decide to split off a “Federal” or “Defense” sub-organization.
Higher levels of CMMC would only apply to systems that contact specific types of data, such as Controlled Unclassified Information (CUI) at level 3+, or design information about classified networks at level 5 (this is a guess), etc.
As organizations need to certify to higher levels, they should try to reduce the number of systems that are in scope. In other words, don’t let your accounting department use the same network as your Missile R&D team. Then audit your general network at level 1 and audit the Missile R&D network at level 4.
This article about how to Identify Scope to an Assessor has graphics and examples of how to identify your scope formally.
Are you looking at a single system, a small isolated network, or all the computers that your business uses?
Worst case: it could be your entire business network including all workstations, servers, and cloud accounts.
The general guidance on scope is that it applies to all systems that have direct connectivity with a system that has FCI / CUI. Essentially, if you have a file server with FCI / CUI, any other system that can manage it, install programs on it, or browse files in it are in-scope.
If you don’t currently have any DoD contracts, it is possible that companies may be allowed to evaluate a temporary and highly secure network just for bidding on RFPs. Check out the Allowable Cost article for more on this topic.
How can I segment my network to reduce scope?
To remove parts of your network from being in-scope, you should have firewalls with deny-by-default rules (in addition to other security) in between your FCI /CUI systems and other systems.
An easy example of effective segmentation is a popular website like Amazon.com
If you are a user of that website, you can still access your needed functionality by connecting with HTTPS over port 443. Your connection goes through a Web Application Firewall to protect the website against common exploit tools.
You can’t access the database or the file system of the web server directly, only authorized administrators can, and even they need to use protected interfaces via the back-end. The web server and back-end systems (database, file server, network, backups) and the administrator’s computer are segmented together. You are outside the segment.
When you are designing segmentation, go for that level of separation that you see from big websites and SaaS clouds. Don’t let anyone reach into your segment from outside (deny all incoming traffic), or if you really need to, only allow specific ports through the firewall (and use a DMZ subnetwork for those externally-connected systems).
3. Review each CMMC practice against your environment
The low cost method is to print out the CMMC requirements and start on the first domain, first practice.
If you want to outsource this to an expert or get guidance on how to comply with specific items, there are plenty of cybersecurity consultants available.
You might use Excel or another spreadsheet program to record your thoughts and status on each capability. See our Templates and Tools page for several great CMMC tracking spreadsheets (free to the public, no registration required).
Industry standard practice is to create a System Security Plan for each organization’s network. A government-recommended template which includes most of the CMMC practices (but not all) can be found on NIST’s Special Publication 800-171 page.
Note: Not all practice IDs will be used. For each domain, the practice IDs increment through Level 1, then Level 2, Level 3, etc. If you are certifying to level 3, you won’t need the practice IDs for level 4 and 5.
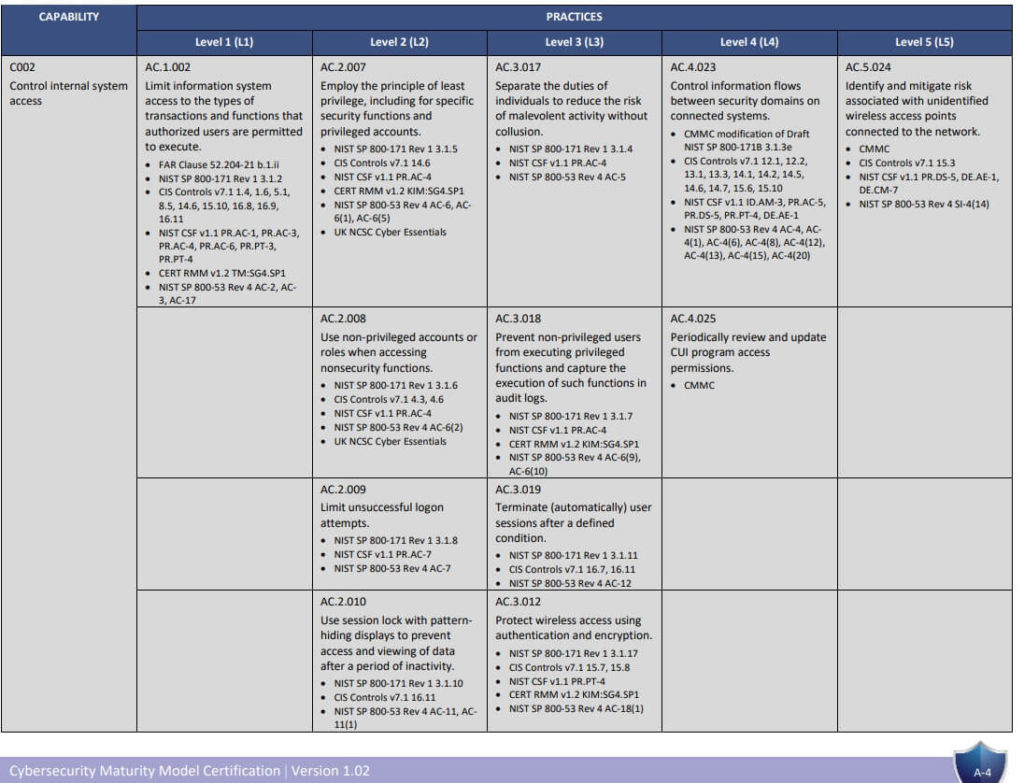
Page A-4 from Cybersecurity Capability Maturity Model Certification Appendixes Version 1.02 dated March 18, 2020
If you are just starting, then I recommend beginning with just the CMMC Level 1 requirements. Once you’ve completed reviewing those, move to the CMMC level 2 requirements, etc. If you are feeling bold, you can lump all the CMMC level 1-3 requirements together and answer them together (or whichever level your organization needs).
Pick an appropriate level of security (see start here first if you don’t know). You need to meet all requirements up to your chosen level. If you choose level 3, you need to meet level 1 and 2 as well.
For each requirement, READ THE CMMC ASSESSMENT GUIDE PAGE for that requirement, then ask whether your network / company / organization is meeting the entire requirement. If yes, make a note on your spreadsheet of some proof (such as a policy name and page number). You can use N/A if your network doesn’t have anything that the capability would apply to. For example, if you don’t allow any remote access, those best practices would be N/A.
In the Assessment Guide, there are several statements called “Assessment Objectives”. These are the exact statements that your environment will be evaluated against. To pass a practice, each Assessment Objective needs to be either “MET” or “NOT APPLICABLE” for that practice. A single “NOT MET” Assessment Objective will cause a practice to be marked “NOT MET” overall.
Depending on your style, you might run through all the requirements without stopping, marking Implemented, Not Implemented, N/A, or Uncertain. Or you might stop and implement each best practice before moving on.
Don’t forget the “Maturity” part of CMMC
Performing cybersecurity with “Mature” processes is much harder than simply meeting the technical implementation requirements in the CMMC. At CMMC level 3, your C-level staff needs to formally assign a budget to cybersecurity. They need to provide enough IT and security staff to perform all the tasks that support CMMC level 3 requirements (this is normally 4 full time IT staff for a 200 person company). They need to hire at least one senior cybersecurity expert who understands compliance and can find gaps. And your C-level staff needs to support cybersecurity by endorsing policies and helping your department to purchase needed security tools and systems.
For each CMMC requirement, brainstorm the activities that need to occur to ensure that requirement is fully implemented throughout your environment now and into the future. You should perform these activities on schedule and capture proof that you are doing them.
You will see in the Assessment Guide that the maturity processes for Level 2 and Level 3 are repeated for each domain. This makes maturity a significant portion of the assessment.
Maturity Processes = 17 domains * 3 processes each = 51 maturity processes to be evaluated.
CMMC ML.2.999 Developing an effective CMMC Policy
CMMC Level 3 Assessment Guide Webinar and Review
CMMC Plan of Action & Milestones POAM
If unsure or your company isn’t doing a practice, make a plan (including timelines) for how you will meet the best practice. This is called a “Plan of Action & Milestones” (POA&M).
If it is impossible to meet a best practice, don’t beat yourself up (for now). Just write a POA&M for that item which includes a description of your current status, a list of steps you will take to resolve it (such as “1. Identify solution that meets requirements”), and estimated timeline for each step.
Gathering evidence for the CMMC
For each “implemented” practice, take a note of where to find evidence that it is working. For example, you might put a link to your policy document for a capability. Or take a screenshot of your current firewall rules. If you’ve marked a capability as “N/A”, write a brief description of why it doesn’t apply to your environment. This evidence will be very important during the 3rd-party audit process.
You need to evaluate each CMMC practice across your entire scope
Let’s use Audit and Accountability “Review and manage audit logs” (C010) as an example.
This capability states “Review and manage audit logs “. For level 2, it states “Review audit logs.”
To implement this, most companies would
- Enable logging
- Write a procedure and/or train admin staff how to access the audit logs
- Using policy, schedule regular audit log reviews.
That sounds simple right? Except you need to repeat this for each device and system in your scope:
- Windows Domain Controller 1
- Windows Domain Controller 2
- File Server
- Firewall
- Switches
- Each desktop and laptop
- Office 365 Email
- Office 365 Sharepoint
- Windows Database Server
- The Quickbooks application installed on the database server
- Windows Utility server
- The antivirus program installed on the utility server
- The backup program installed on the utility server
- and on and on…
Enabling logging across all your workstations, servers, network devices, and cloud accounts is going to take some work. Then you need to review those logs. Even a small network will generate thousands of pages of audit logs per day. At this point, most companies realize they need to implement a system just for capturing and centrally-storing logs to automatically identify problems and provide reports.
Moral of the story: The complexity of your environment greatly affects the level of effort involved. It can be tempting to only consider one system (such as Active Directory or your workstation) when you evaluate a requirement. But if you are doing this correctly, you will assess your practice against your entire in-scope environment.
5. Put together your CMMC assessment package
This is the package you’d review with an auditor. Here are some items it will include:
- Contact information for your Information Security Officer and company.
- Diagrams of your in-scope environment. These diagrams should accurately represent the types of systems in your network, where the borders are, and communication flows in / out / and through your environment.
- Copies of any policies and procedures referenced in your assessment.
- A risk analysis and results from your latest vulnerability scan and penetration testing.
- A summary of the CMMC practices and whether your environment meets each security level or not.
- Detailed report of each CMMC practice. Includes text response and evidence (screenshots, location of artifact, etc).
- POA&M for temporarily deficient practices and continual improvement (past the minimum of your CMMC levels).
5. Double-check your package against the Assessment Guide
As of December 2020, the CMMC Assessment Guides have been released by the DoD.
Review the Assessment Objectives listed for each practice. Review the Assessment Considerations section for each practice. In some cases, this clarification may make you realize that your implementation does not meet requirements.
Review these articles for more information and links to the guides.
CMMC Level 1 Assessment Guide and Review
CMMC Level 3 Assessment Guide Webinar and Review
How to read the CMMC Model…
Requirements for the CMMC are divided into 17 domains
- Examples of domains are: Awareness & Training (AT), Configuration Management (CM), Incident Response (IR), and Physical Protection (PP)
Each CMMC domain contains several cybersecurity best practices which are called “capabilities”.
- For example, the Awareness & Training (AT) domain, has two capabilities.
- Capability: “Conduct security awareness activities”
- Capability: “Conduct training”
- These capabilities are given a unique identifier based on their order in the document. The naming scheme is C001 – C999.
Each CMMC capability has “practices”, which relate to the level-specific expectation for that capability.
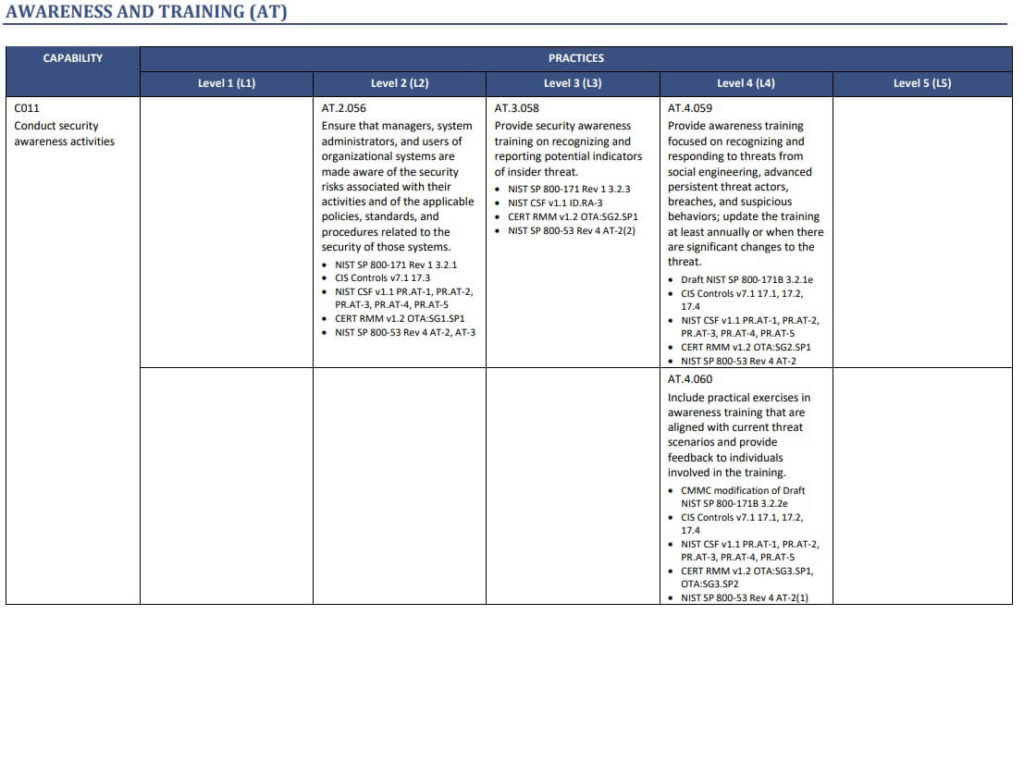
Page A-11 from Cybersecurity Capability Maturity Model Certification Appendixes Version 1.02 dated March 18, 2020
For this exercise, we are looking at capability C011 “Conduct security awareness activities” in the Awareness and Training domain.
C011 + Level 1
There is no practice for C011 and Level 1 (this cell is blank) . In other words, Level 1 businesses do not need to perform security awareness activities in their organization.
C011 + Level 2
C011 + Level 2 (slightly secure network) has a best practice. The practice ID is AT.2.056.
It requires that organizations “Ensure that managers, system administrators, and users of organizational systems are made aware of the security risks associated with their activities and of the applicable policies, standards, and procedures related to the security of those systems”
In other words, Level 2 businesses warn their staff that bad guys exist and where to find policies and procedures for protecting the computer systems.
C011 + Level 3
C011 + Level 3 (secure network with CUI) has a best practice. The practice ID is AT.3.058.
It requires that organizations “Provide security awareness training on recognizing and reporting potential indicators of insider threat.”
In other words, Level 3 businesses warn their employees that internal staff could be security risks too, and how to report concerning behavior.
C011 + Level 4
C011 + Level 5 (secure network with more sensitive CUI) has two best practices. The practice IDs are AT.4.059 and AT.4.060
AT.4.059 requires that organizations “Provide awareness training focused on recognizing and responding to threats from social engineering, advanced persistent threat actors, breaches, and suspicious behaviors; update the training at least annually or when there are significant changes to the threat.”
AT.4.060 requires that organizations “Include practical exercises in awareness training that are aligned with current threat scenarios and provide feedback to individuals involved in the training.”
A contractor with level 4 data might put their employees through a multiple awareness courses each year and give individual feedback to employees in order to prepare them for these advanced threats.
C011 + Level 5
C011 + Level 5 (secure network with extremely sensitive CUI) has no best practice (the cell is blank).
Higher levels inherit all the lower level practices. So a level 3 business needs to both advise their employees about general security risks and give specific training to identify insider threats (level 2 + level 3 requirement). If you are certifying to level 5 and level 5 is blank, you still need to account for level 1, 2, 3, and 4.
CMMC practices reference other standards
Most (or all) practices will reference a control from a different cybersecurity standard. Examples are “NIST SP 800-171 3.2.1” or “CERT RMM v1.2 OTA:SG1.SP1”. You can see this in AT.2.056.
You don’t have to look up every other control listed in the CMMC. They are supplemental information.
If a company has already complied with a different compliance framework (such as Cyber Security Framework), the references can be used to skip practices that are already good.
It is common for IT staff to read a capability and practice and still not understand it. It can help to check other versions of the best practice for clarification.
Steps to find “NIST SP 800-171 3.2.1” as an example
You can see NIST SP 800-171 in the menu above. If you navigate to that menu item, you will find a link to the current NIST Special Publication 800-171 document. Download the document and search for “3.2.1” inside it. You will find the NIST version of the AT1-Level 2 best practice. When you compare the two, you will see that they have a similar goal.
How to read and use the CMMC Model (video)
Check out this article for a very simple webinar from the Software Engineering Institute (authors of the CMMC model) about how to read and use the CMMC model.
Webinar on CMMC Level 1 by the Software Engineering Institute (CMU)
Please contribute!
If you find a good resource, leave a comment. Over time, this website will be a central place we can discuss the CMMC capabilities and share what works.
Please link to this page or share with your colleagues!

Are you aware if the government will offer workshops on the CMMC? How do we get our staff trained for this? (Employees will be working with the auditors.)
Any thoughts on how much a small company can expect to pay for a level 1 assessment?
Hi Nikki,
I’ve heard Government representatives say that level 1 assessments should be in the $3,000 ballpark for a small company. However, I don’t see any indication that the government is planning to set rates for assessments, so it will probably be market driven.