Editor’s note: This in-depth article about the CMMC is written by Tom Sharp from Kelser Corporation, an MSP and IT consulting firm.
If you’re a supplier or manufacturer that relies on business with the Department of Defense (DoD) and the contracts they offer, you will need to ensure that your IT infrastructure can pass a third party certification for cybersecurity readiness over the coming months.
This certification is referred to as CMMC or the Cybersecurity Maturity Model Certification. It is an initiative designed to help protect the data being shared within the Defense Industrial Base of the United States and the contract information necessary to produce the parts, systems, and components needed for our national defense.
If your organization is unable to meet CMMC, it could potentially lead to lost contracts, loss of revenue, and even business closure. You may also be exposing your business to other cyber threats by not taking the steps needed to become compliant. By starting now (if you haven’t already) you’re heading in the right direction to a more secure future.
As VP of Operations for Kelser Corporation – a Connecticut-based MSP and IT Consulting Firm – I’ve spent the better part of two decades learning about IT, cybersecurity, and how to engage with clients and peers in a way where they can turn those into a business advantage rather than a hurdle. I’ve written this article to help make this new set of requirements easier to understand by exploring what the certification is, who is affected, some sense of timing, and actionable next steps to get you started down the path towards a successful CMMC audit.
What is CMMC?
The Cybersecurity Maturity Model Certification or CMMC is a set of policies and practices critical to organizations that support or feed into the Defense Industrial Base (DIB). Partners and suppliers to the DIB will have their cybersecurity posture compared to these criteria to determine how well prepared they are to handle cybersecurity threats and also how well cybersecurity is integrated into their organizational culture.
The outcome of this audit process will be a neutral party verification of the “level” of their cybersecurity readiness – which we will go into later. The main goal of the program is to validate the safeguards and practices that ensure basic cyber hygiene and the protection of controlled unclassified information (CUI) that is present within the supplier and partner networks of the DIB. Initial rollout of the CMMC program will be specific to DoD contracts.
What is the difference between CUI and FCI?
According to the National Archives, CUI or Controlled Unclassified Information is: “information that requires safeguarding or dissemination controls pursuant to and consistent with applicable law, regulations, and government-wide policies but is not classified under Executive Order 13526 or the Atomic Energy Act, as amended.”
Whereas FCI or Federal Contract Information is defined as: “information, not intended for public release, that is provided by or generated for the Government under a contract to develop or deliver a product or service to the Government, but not including information provided by the Government to the public (such as on public websites) or simple transactional information, such as necessary to process payments.”
Here’s a good infographic from the National Archives CUI Program Blog that helps qualify information that is considered FCI, CUI, or Public. Within the construct of the CMMC, know that CUI will require a higher level (3 or higher) of CMMC Certification whereas FCI may only require Level 1 Certification.

Image credit: National Archives CUI Program Blog
What is the timing of the CMMC requirement?
The timing of CMMC becoming a requirement is still in flux. The official CMMC Advisory Board – made up of various higher education, research, and business leaders working to create a methodical and practical timeline for implementation – originally targeted Winter-Spring 2021 for go live on the overall program.
According to the DFARS Case 2019-D041, “By October 1, 2025, all entities receiving DoD contracts and orders, other than contracts or orders exclusively for commercially available off-the-shelf items or those valued at or below the micro-purchase threshold, will be required to have the CMMC Level identified in the solicitation, but which at minimum will be a CMMC Level 1 certification.”
If you think that your business will need to become CMMC certified at any level it would be prudent to start on that path as soon as possible. Depending on your current cybersecurity posture, the steps to become compliant could take months or potentially longer.
Once the DoD begins to assign CMMC level requirements to contracting engagements, those required levels will become criteria for entry into the bidding process. If you’re not at the necessary CMMC level, you could be missing out on potential revenue.
Is my company impacted by CMMC?
The CMMC structure is composed of five levels of certification with Level 5 being the highest:
- Level 1: Safeguard Federal Contract Information (FCI)
- Level 2: Serve as transition step in cybersecurity maturity progression to protect CUI
- Level 3: Protect Controlled Unclassified Information (CUI)
- Levels 4-5: Protect CUI and reduce risk of Advanced Persistent Threats (APTs)
Each level has its own set of practices and processes that also include any in the levels below it. For any partner or supplier on a DoD contract that may be exposed to CUI in their environment a minimum of Level 3 certification will be expected.
There will be partners or suppliers that ONLY produce commercial off-the-shelf products. For those suppliers, CMMC certification will not be required. Also for example, if your company only has access to FCI, that would require certification at CMMC Level 1. Keep in mind that the certification is valid for 3 years so you will need to continually ensure compliance within your CMMC level or adjust as necessary.
The 17 Capability Domains of the CMMC Construct
Within CMMC there exist 17 Capability Domains or areas of focus:
- Access Control (AC) – Establish system access requirements. Control internal system access. Control remote system access. Limit data access to authorized users and processes.
- Asset Management (AM) – Identify and document assets. Manage asset inventory.
- Audit and Accountability (AU) – Define audit requirements. Perform auditing. Identify and protect audit information. Review and manage audit logs.
- Awareness and Training (AT) – Conduct security awareness activities. Conduct training.
- Configuration Management (CM) – Establish configuration baselines. Perform configuration and change management.
- Identification and Authentication (IA) – Grant access to authenticated entities.
- Incident Response (IR) – Plan incident response. Detect and report events. Develop and implement a response to a declared incident. Perform post incident reviews. Test incident response.
- Maintenance (MA) – Manage maintenance.
- Media Protection (MP) – Identify and mark media. Protect and control media. Sanitize media. Protect media during transport.
- Personal Security (PS) – Screen personnel. Protect CUI during personnel actions.
- Physical Protection (PE) – Limit physical access.
- Recovery (RE) – Manage backups. Manage information security continuity.
- Risk Management (RM) – Identify and evaluate risk. Manage risk. Manage supply chain risk.
- Security Assessment (CA) – Develop and manage a system security plan. Define and manage controls. Perform code reviews.
- Situational Awareness (SA) – Implement threat monitoring.
- Systems and Communications Protection (SC) – Define security requirements for systems and communications.
- System and Information Integrity (SI) – Identify and manage information systems flaws. Identify malicious content. Perform network and system monitoring. Implement advanced email protections.
Each of these areas will be further defined by controls which describe process or practice against which your company will be validated. Depending on the level of maturity in the model, there will be increasing number of controls for each domain.
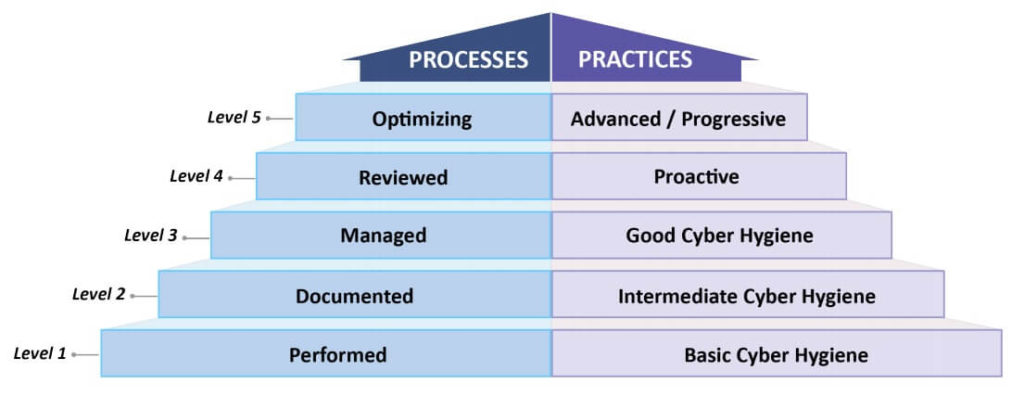
Image credit: CMMC Model version 1.02, page 4
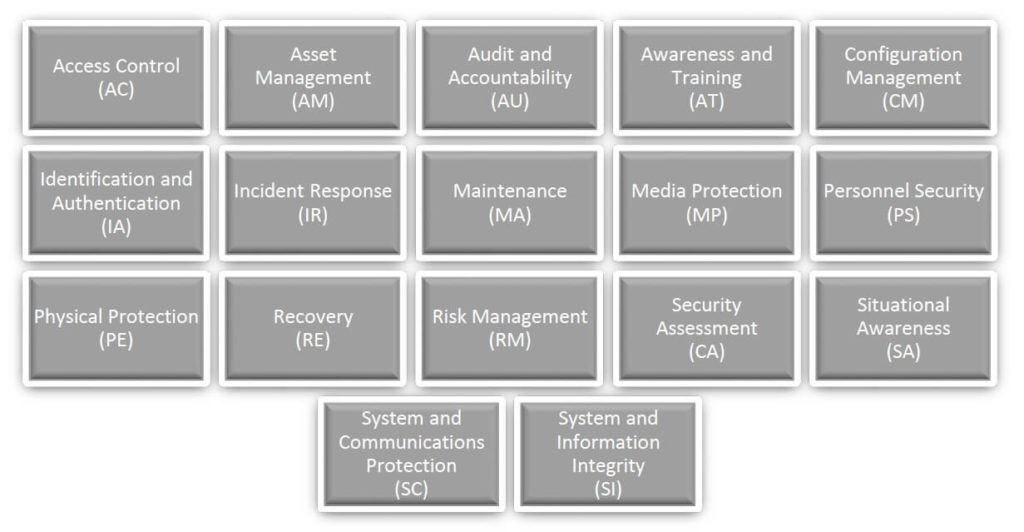
Image credit: CMMC Model version 1.02, page 7
Through the achievement of the various controls – either practices or processes in place – your organization’s “level” will be determined on a scale of 1-5 as discussed in the section above. Each level builds upon the prior and represents further maturity towards significant cybersecurity readiness.
As we look at the policy and practice progression building from lowest to highest, we see a logical growth in the number of practices needed to achieve higher levels. We also see how much more ingrained in the organizational culture these practices and their supporting processes have become. It is not enough just to have all the cutting-edge technology in place, but rather that the understanding of, use, testing, and optimization of these solutions be part of the day-to-day operations of your business.
This chart shows the progression of the processes within an organization as it matures from Level 1 to Level 5. Note how we begin with simply having processes in place to documenting, plan/use, review/measure, and finally optimizing.
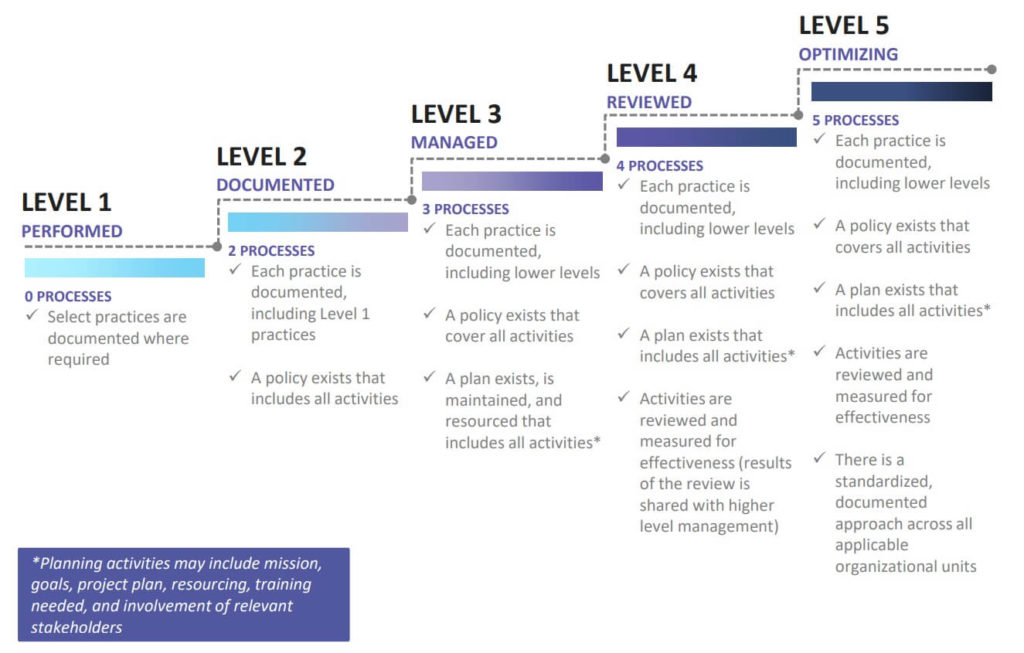
Image credit: CMMC Model Briefing
Similarly we see below how the number of practices in place grow with the levels. Note that CMMC is built upon existing foundations and practices such as NIST and FAR. CMMC represents a means by which to validate and certify these are now in place where other models may have been self-certified.
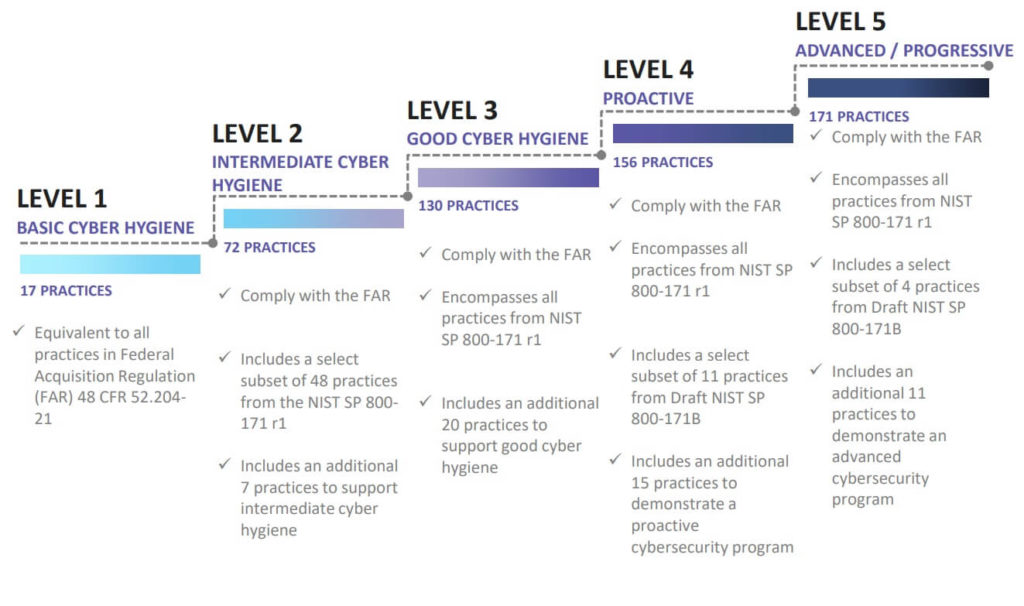
Image credit: CMMC Model Briefing
How can I become compliant with CMMC requirements?
As mentioned earlier, the full requirements for adherence to CMMC as the basis of contract eligibility have not been put in place yet. But consider that some of the changes necessary to become aligned to the framework will take some time to implement and become part of the company culture. The best practice would be to start now and begin down a path of assessing gaps, finding best practices, remediate as necessary, test and re-assess.
Here’s a basic idea of what this could mean to a supplier or partner:
- Determine whether you handle CUI or FCI and confirm the appropriate “level” to target for certification
- Audit-readiness assessment – compare your current practices and processes with those outlined in the CMMC structure for that appropriate level
- Make a plan of attack to remediate any gaps – consider impact, budgeting, cultural shift, time to implement and progression towards the target
- Document new processes and practices
- Test, validate, and document results
- Engage a 3rd Party Certified Auditing Organization (3PCAO) to execute the formal audit
- Resolve remaining gaps and finalize your audit
- Stay engaged with an IT managed service provider (MSP) to ensure periodic validation of your progress
If you’re unsure, it’s okay to bring in help
There are many resources available online beyond this article to help you work towards CMMC, but they may only go so far to help you if you are unsure what to do next.
Start by evaluating your internal team:
- Do they have extensive experience with cybersecurity?
- Can they adequately execute and maintain each of the 17 capability domains for your level?
- How will taking this on impact your current resources? Will you need to bring on additional team members to maintain certification?
If you currently work with an IT managed service provider, you can ask some similar questions about their capabilities as well as evaluate your current agreement with them and what it provides.
You’ll also want to examine their cybersecurity capabilities, experience, and certifications. Though they may be able to check some or all the boxes you’ll need for CMMC, it could all be for naught if you suffer a data breach or ransomware attack and don’t handle it properly.
If you’ve reviewed your internal and external resources and find that you aren’t comfortable or confident in the solution they can provide for CMMC-related services, consider evaluating other IT managed service providers. Since CMMC wasn’t likely a consideration when you brought on your current provider, it’s understandable that you may need to explore other options to meet compliance.
When considering a new managed service provider there are some best practices to keep in mind including some must-answer questions for you internally as well as the MSP that you are considering. Look for recommendations from colleagues or groups that you’re affiliated with to get your search started and the internet can also be valuable here as well. You can search for highly reviewed MSPs as well as “best” managed services providers near you.
The work that will be required for CMMC is best handled by a local MSP that can become intimately familiar with the specific needs of your business. Having a trusted, local, reliable MSP to partner with is critical especially when dealing with some of the CMMC cybersecurity areas like incident response and testing. If you’ve worked with an outsourced MSP previously, you’ll likely see an immediate difference when pivoting to a local partner.
Remember that when working with an MSP and exposing your network to their systems, that partner needs to certify to the same CMMC Maturity Level as your organization for the protection of FCI and CUI.
Should you have questions or want to continue the conversation, connect with me (Tom Sharp) on LinkedIn or reach out directly at tsharp@kelsercorp.com. You can also learn more about my organization at www.Kelsercorp.com and pick up additional information like ebooks, videos and blog posts in our Learning Center.
Next articles:
CMMC Compliance FAQs – Organizations seeking certification

Hi. With Covid etc. will CMMC assessments by C3PAO with clients be allowed to be conducted virtually?
What will a C3PAO be able to charge for certifications at levels 1, 2 & 3?