Several peers from the CMMC ecosystem (C3PAOs, provisional instructors, provisional assessors, and a leader from the defense manufacturing community) collaborated to create a detailed analysis of the CMMC Scoping Guide for Level 2.
This analysis contains 12 scenarios which illustrate different common architectures used by Organizations Seeking Assessment (for better or worse). It asks the reader to make specific determinations about scoping, boundaries, separation, and applicable practices. Then it provides recommended answers and analysis for each scenario from a CMMC assessor’s viewpoint.
As you read this analysis, you will realize that many questions are not answered definitively by official guidance from the Department of Defense. In order to reach standardization of assessment and prevent unnecessary cost and re-work, all CMMC assessors and OSCs need to be on the same page about these topics.
Until the Department of Defense provides clarification, this analysis proposes ways to interpret the guidance we do have in a standard way. We hope the Department of Defense will supply clarifications to these topics soon.
Topics addressed:
- Is ciphertext CUI?
- Are all practices subject to inspection for Security Protection Assets?
- If Operational Technology contains CUI, is it subject to inspection?
- Are government networks in-scope since they have CUI in them?
- Are systems that provide redundancy considered Security Protection Assets?
- What systems of a Managed Service Provider are in-scope?
- Is VDI an effective boundary?
- Can OSCs use a single directory for both their enclave and corporate network?
- How would multiple assessments for a single organization be scoped?
Download the paper here (PDF)
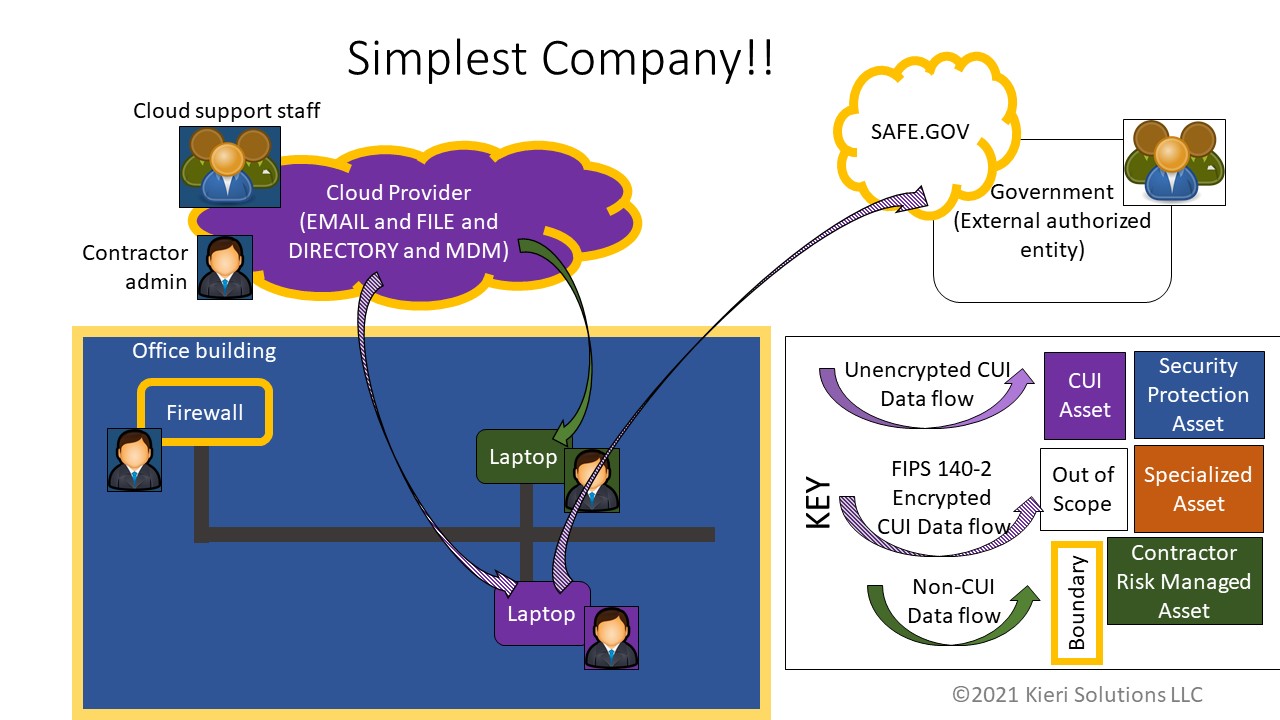
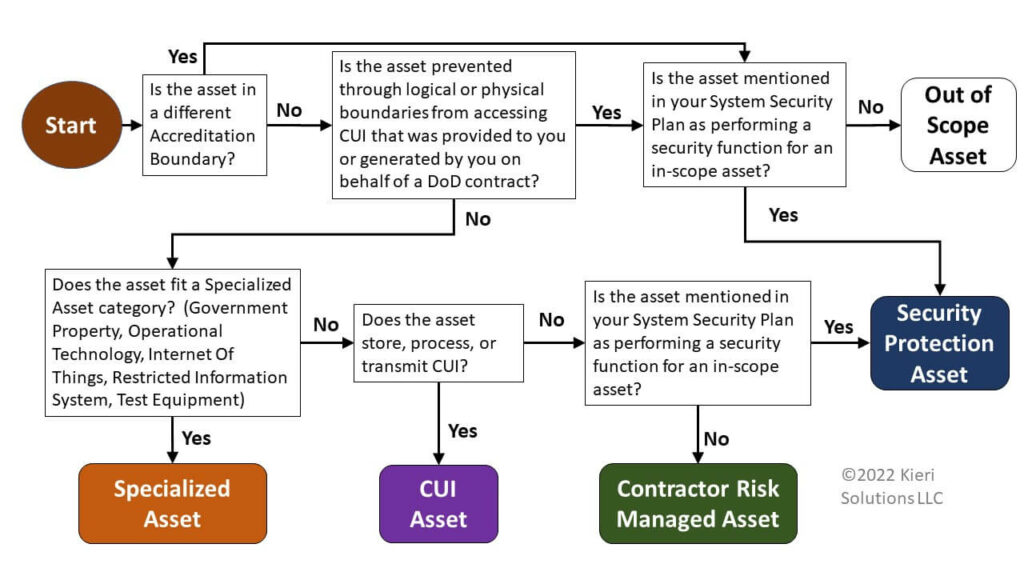
Below is a key diagram from the scoping scenarios analysis. We hope you get value from all 12 scenarios within it!
Thank you to Kieri Solutions for coordinating this analysis and to Amira Armond as the primary writer and scenario designer. Kieri Solutions is an Authorized C3PAO and offers CMMC assessment services for defense contractors and their service providers.
Thank you to the contributors: Allison Giddens (Win-Tech, Inc.), Jeff Baldwin(Space Coast Cyber), Joy Beland and Brian Hubbard (Edwards Performance Solutions), Vince Scott (Defense Cybersecurity Group), and Nathan Regola (Regola Cyber).
Please sign up for our newsletter so that we can let you know when there are significant changes to CMMC or noteworthy articles published! No spam guaranteed. We do not share your contact information with anyone else.