After almost a year of silence, the DoD has released major updates to the CMMC program.
Here is an analysis of the changes, and reference links to the official sources.
48 CFR Chapter 2 – Cybersecurity Maturity Model (CMMC) 2.0 Updates and Way Forward
The source document was revoked almost immediately after it was put onto the Federal Register this morning (November 4th, 2021). Here is a link to a downloaded version.
This release states that CMMC is being changed to version 2.0 with the following major changes:
Eliminate CMMC level 2 and 4
Level 2 has been a joke since the beginning of CMMC. The DoD publicly stated that they didn’t see any reason to ever require level 2 on a contract. This simply removes unnecessary bits that everyone has been ignoring anyways.
Removing CMMC-unique practices
This means that CMMC Level 3 will only require the controls in NIST SP 800-171.
This aligns CMMC with other regulations which require 800-171. For example, a Federal level notice from ISOO states that only NIST SP 800-171A will be used for assessment of non-federal organizations holding CUI.
Removing all maturity processes from the CMMC model
The Maturity Processes added by CMMC were a + 50% to +100% level of effort for businesses. They were poorly defined – in the full year after release of CMMC version 1, the DoD never provided an example of a passing policy, procedure, or plan. This resulted in DIBCAC assessors enforcing written step by step procedures for each Assessment Objective in the CMMC Assessment Guide.
This was the #1 reason for C3PAOs to fail their CMMC assessment according to the October 2021 Town Hall. I don’t think the creators of CMMC actually intended for defense contractors to write 300-500 pages of step by step procedures for an Assessment Guide, but this is what ended up happening. When companies with every advantage (C3PAOs have provisional assessors with special training, fully dedicated to CMMC, and overabundance of cybersecurity staff) cannot pass their CMMC assessment because of “process maturity”, it spells doom for defense contractors.
Allowing annual self-assessments with an annual affirmation by DIB company leadership
for CMMC Level 1;
Good luck with that. We’ve already seen the level of cybersecurity performed by DIB when it isn’t enforced by third party audits. This should be interpreted as the DoD just doesn’t care about protection of FCI and can save a lot of heartache and strife by leaving it status-quo.
Bifurcating CMMC Level 3 requirements to identify prioritized acquisitions…
The full text is “Bifurcating CMMC Level 3 requirements to identify prioritized acquisitions that would require independent assessment, and non-prioritized acquisitions that would require annual self-assessment and annual company affirmation;”
This one is tricky to analyze.
On one hand, this statement and the overall document means that third party assessments is NOT going away.
On the other hand, it means that instead of the estimated 30% of defense contractors needing a CMMC Level 3 assessment (between 30,000 companies and 90,000 companies), maybe only companies handling Controlled Technical Information, Export Controlled, and Nuclear information would need third party assessment.
Those three categories of CUI still makes up a LOT of companies.
Or perhaps it will be based on the contract’s DPAS score. What is a DPAS score you ask? Here is the source: https://www.dcma.mil/DPAS/
More information about DPAS (training slide deck)
There will be a lot of uncertainty as a result of this statement (unless new releases clarify it). This will be used as an excuse not to prep for CMMC.
CMMC Level 5 requirements are still under development
No change here. Anyone who was “in the know” could tell you that CMMC Level 5 wasn’t anywhere close to being enforced due to lack of assessment criteria, lack of training, lack of assessors.
There had been some speculation that DIBCAC would focus on assessing CMMC Level 5 based on their prioritization of contracts over the last year. This seems to be confirmed based on other news releases.
Development of a time-bound and enforceable Plan of Action and Milestone process
Great news! This means that defense contractors don’t have to be perfect in order to pass their assessment.
Using a time-bound and enforceable POA&M would probably follow the model that the federal government uses for their own networks:
- You do the best you can to meet all the requirements
- If you have a situation that you can’t fix right now (cost and effort are not good excuses, but a critical product that doesn’t support a requirement is a good excuse), you can create a POA&M which has the steps and dates for resolution.
- The POA&M items are rated by severity.
- With open high-severity POA&M items that legitimately cannot be fixed through reasonable cost or effort, you can get an “interim” certification.
- Then you have to get re-assessed in a short timeframe, such as 6 months or 12 months, until you resolve the POA&M items.
- During re-assessment, if you don’t make progress on your POA&M items, your certification will expire.
Development of a selective, time-bound waiver process, if needed and approved
This is for situations where the defense contractor has a system that is needed to perform the contract, but the system cannot be secured. Or (more likely) for situations where the defense contractor just completely fails their cybersecurity audit but the DoD decides the contract is mission critical and kicking the contractor off the contract would be too harmful.
For those companies that think they are too critical to fail – this probably also means that you will be subject to independent assessments and perhaps the highest level of requirements.
The CMMC 2.0 program requirements will not be mandatory until…
The full text is “
“The CMMC 2.0 program requirements will not be mandatory until the title 32 CFR rulemaking is complete, and the CMMC program requirements have been implemented as needed into acquisition regulation through title 48 rulemaking.”
Title 32 CFR relates to Federal-level regulations for National Defense. This does not mean that CMMC now applies to the entire Federal government. It is in the section that applies to the Department of Defense. Title 32 CFR is where other cybersecurity requirements live (such as the mandatory cyber incident reporting requirements).
Title 48 CFR relates to Federal-level regulations for Acquisitions. This is where instructions to acquisition and procurement officers about how to manage contracts are kept.
Yikes. How long will that take?
It sounds like the rulemaking can take 9-24 months ( late 2022 through late 2023). But then… it could become mandatory according to this statement. Would it be mandatory for all contractors at once? There is no mention of a phased rollout. This could mean a faster deployment than CMMC’s original timeline.
New DoD website for CMMC 2.0
https://www.acq.osd.mil/cmmc/model.html
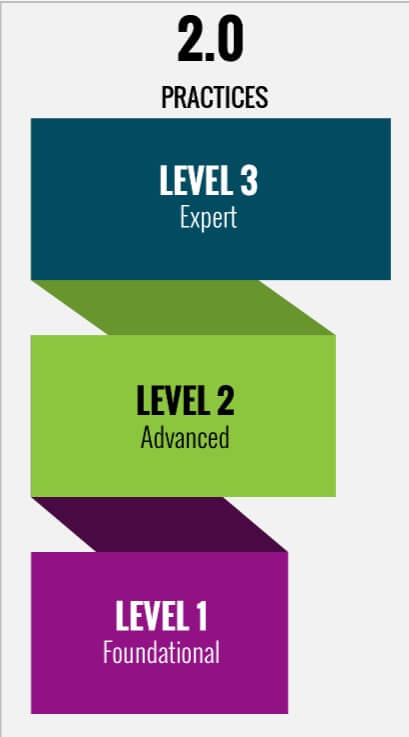
This diagram shows the five levels of CMMC moving to three levels. The baseline for CUI protection is now “Level 2”.

https://www.acq.osd.mil/cmmc/model.html
CMMC still includes Third Party assessment
Once CMMC 2.0 is implemented, contractors will be required to obtain a third-party CMMC assessment for a subset of acquisitions requiring Level 2 (“Advanced”) cybersecurity standards that involve information critical to national security.
The CMMC-AB will accredit CMMC Third Party Assessment Organizations (C3PAOs) and the CMMC Assessors and Instructors Certification Organization (CAICO). Accredited C3PAOs will be listed on the CMMC-AB Marketplace. The DIB company will be fully responsible for obtaining the needed assessment and certification, to include coordinating and planning the CMMC assessment. After the completion of the CMMC assessment, the C3PAO will provide an assessment report to the DoD.
As part of the CMMC 2.0 implementation, the DoD will approve all CMMC-AB conflict of interest related policies that apply to the CMMC ecosystem. Additionally, the CMMC-AB must achieve compliance with the ISO/IEC 17011 standard prior to accrediting C3PAOs and a CAICO. Separately, C3PAOs will be required to comply with ISO/IEC 17020 and the CAICO will be required to comply with ISO/IEC 17024 requirements.”
Some CUI contracts will not require third party assessment
https://www.acq.osd.mil/cmmc/assessments.html
Likewise, a subset of programs with Level 2 (“Advanced”) requirements do not involve information critical to national security, and associated contractors will only be required to conduct self-assessments
https://www.acq.osd.mil/cmmc/assessments.html
CMMC-AB remarks and clarification about CMMC program
A lot of people are asking “What happens to those companies and individuals that invested in CMMC training and titles like LTP, LPP, C3PAO, RPO?”
I’m already getting questions about whether students should cancel their scheduled CCP exam.
Matthew Travis (CEO for CMMC-AB) is quoted by BusinessWire today stating:
Moreover, as we continue our exclusive partnership with DOD in this effort, I am most encouraged by the Department’s commitment to the Interim Program in which CMMC Certifications will be authorized, incentivized, and honored for those DIB companies who elect to pursue certification before the formal CMMC mandate is codified. We want to get those started soon and I expect the market demand for CMMC Certification to be significant.
https://www.businesswire.com/news/home/20211104006007/en/CMMC-Accreditation-Body-Endorses-Pentagon%E2%80%99s-Proposed-Implementation-Changes-in-CMMC-2.0
The CMMC-AB is holding an out-of-cycle Town Hall to discuss the changes on November 9th. Registration link here.
Defense article introducing changes (high level)
Not much unique information here.
What do defense contractors do now?
Well, you can stop writing CMMI-quality step by step procedures and plan. But don’t forget that you still need normal levels of policies and procedures per Appendix E of NIST SP 800-171. Just not to the extreme level that CMMC version 1.0 had introduced.
You can stop reading the CMMC Level 3 assessment guide and start reading the NIST SP 800-171 and NIST SP 800-171A guides instead, at least until new guides are released for CMMC.
You are STILL responsible for implementing the cybersecurity requirements in NIST SP 800-171 if you handle CUI. But wait, you say, they won’t audit me, so I don’t need to… right? Wrong. The government is making a solid foundation for prosecuting contractors under the False Claims Act by bringing requirements back to baseline. They are requiring high level executives in the organization to personally attest to performing cybersecurity. And they are removing the phased rollout.
This all means that if your company is lax on cybersecurity, the government can pursue a false claims case against you. This could come to the government’s attention due to one of your employees making a complaint. This is known as a qui tam lawsuit and is designed to give the whistleblower a portion of the penalty.
It also means that if the government wants to, they can decide your contract needs independent assessment without any warning, because “You said you were compliant”.
You are STILL responsible for implementing the basic cybersecurity requirements in FAR 52.204-21 if you have Federal Contract Information.
Check back for more information about whether you are likely to be third party assessed based on your contract, and for timelines that assessments will start.
What is next?
This is breaking news today, with more information coming out every few minutes. Sign up for our newsletter for updates and commentary as they are released.
Any thoughts on the CMMC Appendices document ? Is that OBE like the other CMMC 1.0 documentations? We’ve used it for clarification, examples, etc. Should I just refer to the assessment guides instead? Thank you!
Hello Beth,
Everything in the CMMC Appendices document was updated over time except 1) the glossary, and 2) the mapping tables between CMMC and 800-53 etc. The CMMC 2.0 Model document replaced the mapping tables so I wouldn’t refer back for that anymore. The only thing that hasn’t been replaced with a more authoritative version is the glossary.
NIST Handbook 162, some of which is included in the current CMMC L3 AG will still be useful.
Thanks for those inputs Amira…! It really helps…!
Amira,
Excellent summary of CMMC 2.0; I always enjoy reading your work!
You say that “You can stop reading the CMMC Level 3 assessment guide and start reading the NIST SP 800-171 and NIST SP 800-171A guides instead, at least until new guides are released for CMMC.”
For me, I find the CMMC Level 3 assessment guide to be useful as it contains the same wording from both the NIST SP 800-171 and 171A while including additional discussion and examples. I’m thinking that the new assessment guide will remove the *.*.997, *.*.998 and *.*.999 sections, include (hopefully) a scoping guide (Appendix A) and not change the assessment objectives since these come from the NIST SP 800-171A . So for me the CMMC assessment guide is helpful for reviewing compliance with the NIST 800-171 controls as it consolidates the information from two documents while providing additional information. What do you think? Am I missing something?
Thank You!