It is time, finally, to talk about the #1 “Other than Satisfied” requirement in 800-171, per historic DIBCAC assessments.
?
? ? ???? 140-2 ????????? ??????? ? ?
?
Listen up – I’m going to tell you how to succeed at this requirement. It might take money, it might take time, but it CAN be done. It will definitely take more than one post though <grin>.
???? ?? ?????
It is a Federal Information Processing Standard ( number 140-2 ) which sets requirements for how awesome a cryptographic module needs to be to pass “validation”.
???? ?? ? ????????????? ???????
NIST’s definition: The set of hardware, software, and/or firmware that implements security functions (including cryptographic algorithms and keygeneration methods) and is contained within a cryptographic module boundary.
Amira’s (hopefully easier) definition: A self-contained software program that has inputs, outputs, a cryptographic algorithm that encrypts data, and the logic required for the algorithm to operate in a predictable way. It can be part of firmware, part of an operating system, or a portion of a larger application.
???? ?? ??? ???? “???????”…?
NIST has very smart cryptologists try to figure out ways to break the encryption from submitted modules. Based on how long it takes for new modules to get validated, my theory is that they spend a couple ????? attempting to find a flaw. If they can’t find a flaw, the module gets a certificate hosted on the NIST website saying it is awesome… err, validated.
?? ???? ?? ??? ???? ?? ?????
The US Government has to transmit secret data across lines that adversaries have access to. Consider messages from our embassies in rival countries. If the other governments are on the ball at all, they will be trying to listen in.
FIPS validation gives the US Government confidence that their secret communications won’t be vulnerable to eavesdropping because the encryption has been tested.
People have invented lots of cryptographic algorithms and modules that turned out to be flawed. It makes sense that the US Government would decide to only use tested modules – it only takes getting burnt a few times to start having an opinion.
And if it is good enough for secret data, it should be good enough for CUI, right?
Question for everyone – have you heard of other cryptography being acceptable to DIBCAC? So far I’ve only heard of people passing this requirement using FIPS 140-2 validated modules. Using a cryptographic algorithm like AES 256 by itself is no good. I haven’t heard of anyone passing using NSA-approved cryptography.
FIPS continued – ???????? the need for FIPS 140-2 validated modules.
Source requirement: 3.13.11 ?????? ????-????????? ???????????? ???? ???? ?? ??????? ??? ??????????????? ?? ???.
There are a handful of requirements in 800-171 that relate to FIPS. It is important to realize that just because FIPS validated cryptography could be used to solve them, it isn’t the only solution.
3.1.13 Employ cryptographic mechanisms to protect the confidentiality of remote access sessions.
^^ Not specific to CUI. Some sort of encryption needed, but FIPS for your remote access sessions (aka VPNs) is only needed if your CUI would otherwise be transmitted in the clear.
3.1.17 Protect wireless access using authentication and encryption.
^^ Not specific to CUI. Encryption needed, but FIPS is only required if your CUI would otherwise be transmitted in the clear.
3.8.6 Implement cryptographic mechanisms to protect the confidentiality of CUI stored on digital media during transport unless otherwise protected by alternative physical safeguards.
^^ This allows physical safeguards instead of FIPS – using a courier instead, for example.
3.8.9 Protect the confidentiality of backup CUI at storage locations.
^^ This allows ??? solution that protects confidentiality of backups, not just encryption.
3.13.8 Implement cryptographic mechanisms to prevent unauthorized disclosure of CUI during transmission unless otherwise protected by alternative physical safeguards.
^^ This allows physical safeguards instead.
3.1.19 Encrypt CUI on mobile devices and mobile computing platforms.
^^ This is the only requirement which explicitly makes a connection between CUI and using encryption.
???????????:
????: You have to use FIPS 140-2 validated modules for all of the above requirements.
????: FIPS is only required if encryption is used to protect CUI.*
*If you don’t transmit or store CUI in that situation, then you don’t need to use FIPS.
*In most cases, you can physically protect CUI instead of encrypting it.
*If your CUI is already thoroughly protected using one layer of FIPS encryption (such a FIPS-protected HTTPS session), you don’t need to double-FIPS-encrypt it (you don’t need to put that HTTPS traffic through a FIPS-enabled VPN too).
????: If you don’t use FIPS 140-2 validated modules for each of these requirements, you fail each requirement.
????: If you don’t use FIPS 140-2 validated modules to protect CUI, you fail only 3.13.11 (the one that says to use FIPS).** Non-FIPS encryption is fine to pass the other requirements.
**Based on DIBCAC precedent.
Please enjoy ⚡️Jil Wright‘s and my somewhat silly video that illustrates these architectural concepts with drawings.
Part three of FIPS 140-2 compliance. ????????????? ???? ???? ?????.
We are almost done with the analysis of the top 10 “Other than Satisfied” #nist800171 requirements according to the DoD’s assessment group DIBCAC.
Now that you understand why FIPS is important to the government, and when FIPS is ??? required, it is time to talk about how to implement it (and demonstrate proof for assessors that you did so).
High level steps:
1. Identify where your CUI is and what systems it passes through.
2. Document these data flows (storage and transit) and identify the protection method used (encryption, physical).
3) For each encryption method, implement a FIPS-validated module or research to find which one is already used.
4) Link or download the certificates for each.
1. ???????? ????? ???? ??? ?? ??? ???? ??????? ?? ?????? ??????? – ?? – ???? ??? ??? ???? ?? ?? ??.
Document a table for CUI in storage and a table for CUI in transmission, and fill in the details for your environment.
You need A) a method to receive CUI from external people; B) a place you can view and edit CUI internally; C) a method to send CUI to external people.
If your CUI is out of control or you don’t know what is CUI (sadly, most contractors are in this position), an approach is to pick one standard way that everyone in your org will be told to store and transmit CUI. Make sure that method is functional and easy to perform, then train everyone on it. Over time, make it the ???? way that CUI is stored or transmitted.
2. ???????? ????? ???? ????? (??????? ??? ???????) ??? ???????? ??? ?????????? ?????? ???? (??????????, ????????).
Add a column to your storage and transmit tables that identifies how the data is protected (encryption or physical). If physically protected (pro-tip: data that stays inside FedRAMP moderate or high clouds can be assumed to be physically protected), then you’re done. If encryption is used to protect the data, then move on to the next step.
3) ??? ???? ?????????? ??????, ????????? ? ????-????????? ?????? ?? ???????? ?? ???? ????? ??? ?? ??????? ????.
The video below is from our Kieri Compliance Documentation public demo.
The time-stamp in the link is the section where ?? ???? ??? ??? ??? ???? ???? ?????????????. You can see examples of how to document your data flows for storage and transit, as well as identifying the cryptographic product and FIPS modules. We were told by our DIBCAC assessors that this was the best FIPS documentation they had ever seen.
Even if you aren’t a customer of Kieri Solutions this demo video is a great source of training about #CMMC documentation best practices.
FIPS 140-2 compliance for #cmmc. ??????? ???????? ????????.
We are at step 3 – research to implement FIPS validated modules:
3) ??? ???? ?????????? ??????, ????????? ? ????-????????? ?????? ?? ???????? ?? ???? ????? ??? ?? ??????? ????.
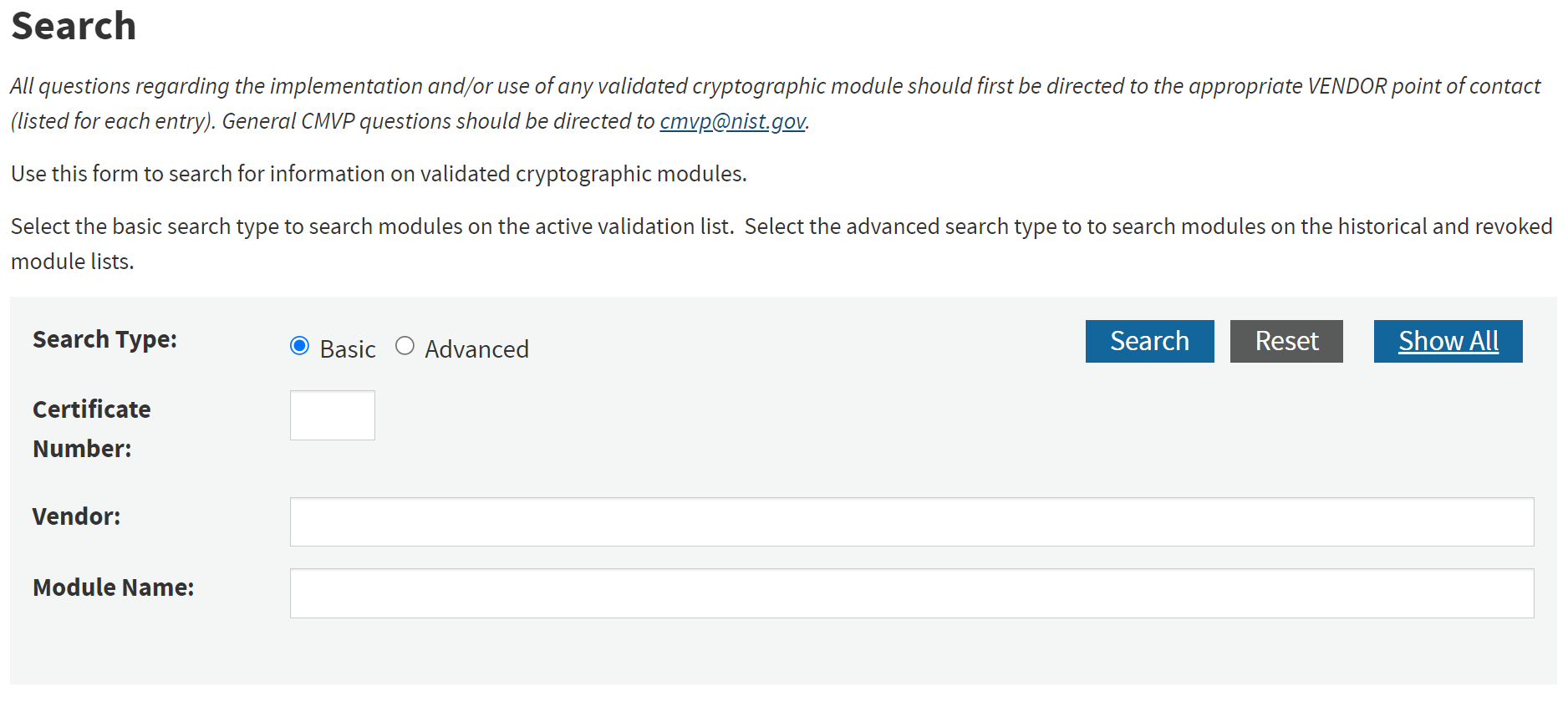
If you already have a solution in mind (such as your existing corporate firewall), the next step is to visit NIST’s Cryptographic Module Validation Program (CMVP), specifically the Search page: https://lnkd.in/gtC9ixuJ
Search for the solution you are using / intend to use. Pro tip: It is normally most productive to search by Vendor.
Validate that your solution has an active certificate, and review the text of it. Almost all certificates will state “When operated in FIPS mode”. You need to figure out how to turn this setting on for your solution.
If you don’t have a solution identified yet, you can use the CMVP to find one.
?? ??? ????? ?????? ????????!! Vendor websites are notorious for misrepresenting their solution’s validated status. If you can’t find a certificate on the CMVP, the solution probably isn’t validated.
I use vendor information to help me find the relevant certificate in the CMVP (for example, Microsoft has a nice KB that links directly to the certificates). Vendor information is also helpful to understand which module is used or how they are used, in cases where multiple validated modules exist for a product.
4) ???? ?? ???????? ??? ???????????? ??? ????.
Exactly what this says – for your 800-171 or CMMC Level 2 assessment, you must provide the ???????????? for each solution to your assessor. Remember last post – you need to show how you are using validated modules for each transit or storage data flow that is protected using encryption.
https://csrc.nist.gov/projects/cryptographic-module-validation-program/validated-modules/search
Don’t forget to document how you turned on FIPS mode (or how to validate it is turned on).
What about cloud use? You need to show that your clouds are also protecting CUI in transit or storage. This is typically done by referencing the cloud’s FedRAMP authorization status (moderate+ includes FIPS).
—
We’ve finally reached the end of the “Top 10 Other than Satisified” #nist800171 requirements according to the Defense Industrial Base Cybersecurity Assessment Center (DIBCAC)!
I hope you enjoyed this series. My next educational effort will be a series of interviews with companies that have successfully passed a CMMC or NIST SP 800-171 assessment. I ask them to describe their solution to specific requirements so that everyone can learn precedent: what is proven to be successful in the past. If you haven’t, follow me or sign up for the newsletter so that you don’t miss the fun.
For FIPS validation can a organization use NIAP- https://www.niap-ccevs.org/products along with CSRC? I know that DIBCAC has stated you can use either one.