Multifactor Authentication: #2 of the top 10 “Other than Satisfied Requirements” for 800-171 assessments by DIBCAC.
??? ??????????? ?????????????? ??? ????? ??? ??????? ?????? ?? ?????????? ???????? ??? ??? ??????? ?????? ?? ???-?????????? ????????.
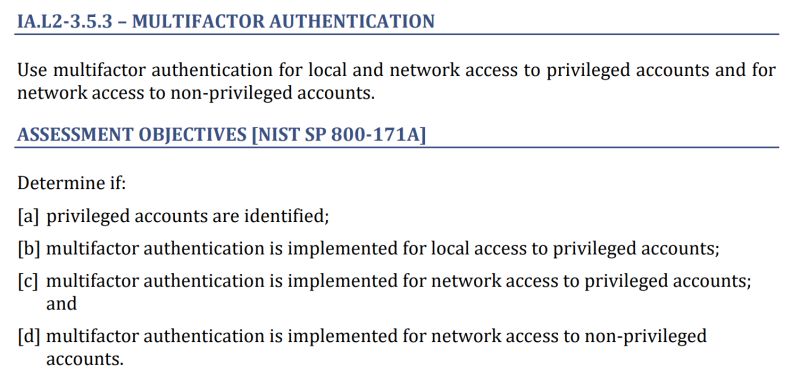
My theory is that most of the time when this requirement is failed, it is because the IT department didn’t know about the Assessment Objectives (AOs) so they were surprised during the assessment. See the picture below for the full list of Assessment Objectives.
When most people read this requirement, they think of the MFA available from their cloud providers. For example, many defense contractors have MFA through Azure Active Directory / Office 365 which displays an MFA challenge when they connect to it. Unfortunately, MFA from your cloud only handles two of the four Assessment Objectives (the ones that say “network access”).
What is this applicable to? Workstations, servers, and potentially even network devices. Especially for devices that are considered “CUI Assets”, though I think that most assessors feel MFA is applicable to any accounts in a directory that manages access to CUI.
Think that logging on from a specific location counts? Or that your laptop is “something you have?” Think again. Those won’t pass.
Where do companies go wrong? #1: They forget that one of the AOs requires MFA for ?????????? ????? logon.
What is ?????? This means logging in with an account where authentication traffic does not traverse a network. Think cached credentials or accounts stored on the device.
What is ??????????? An account with admin rights, such as root, administrator, or your personal admin account.
Common solutions for MFA for ?????????? ????? logon? Fingerprint scanners ??, smart-cards or pluggable drives with certificate logon ?, or time-based authenticator codes ?.
Where do companies go wrong? #2: They don’t address the full scope of their environment.
I’ve heard second-and-third-hand stories of DIBCAC assessors failing companies because their firewall administrator console didn’t prompt for MFA. The stories are horror genre because it is hard to find firewalls that have the ability to support MFA.
?
Common solution for devices that don’t support MFA: Implement a “Privileged Access Workstation”, “Bastion host”, or “Jump box” which prompts for MFA before you can connect to the administrative console for firewalls, Linux servers, and other devices that don’t easily support MFA. If your firewall can be administered from outside, lock that down.
I expect a few people are hyperventilating into a paper bag after reading this. Would love to hear your thoughts, solutions, and stories about MFA. Is it true that MFA has been expected on network devices? What about printers?