An unanswered question in CMMC is whether assessors will be expected to hold the line on Controlled Unclassified Information (CUI) regulations that are not specific to CMMC.
CUI Specified and CMMC
Depending on the type of CUI your business handles, you may be required to protect it in “specified” ways, which is where the CUI//SP label comes from. Specified protections can be found in the attachments for each category at National Archives:
https://www.archives.gov/cui/registry/category-list
For example, if you handle Unclassified Controlled Nuclear Information – Defense (CUI//SP-DCNI), you should read the CFR-2018 Title 32 Volume 2 Part 223. The CFR is extremely restrictive about who can receive this information and describes specific requirements like not discussing CUI//SP-DCNI over unencrypted phone lines except “in an emergency”.
https://www.govinfo.gov/content/pkg/CFR-2018-title32-vol2/pdf/CFR-2018-title32-vol2-part223.pdf
Should an assessor fail a business if they violate handling requirements for their Specified CUI? Should an assessor double-check the regulations for the CUI being assessed? Or is this beyond what is expected?
Define procedures for the handling of CUI data
The CMMC Level 3 practice AM.3.036 looks like it holds the answer. It requires that organizations “Define procedures for the handling of CUI data.” The discussion states “The contractor defines and establishes procedures for the proper handling of CUI. These procedures, while defined by the contractor, must be in compliance with applicable government laws and regulations.“
Based on this practice discussion, I would expect an assessor to understand applicable regulations and check the organization’s compliance with them, as related to their procedures.
From a practical standpoint, most assessors are not going to go deep into the weeds of every regulation. They are not easy to read and their guidance is often open to interpretation. While I haven’t read every CUI-Specified regulation, so far I haven’t seen any that stipulate technical information system protections beyond what CMMC Level 3 requires.
The Export Controlled category of CUI, which includes International Traffic at Arms (ITAR) data, is noteworthy because it requires administrative protections like preventing non-US persons from accessing the data. I expect that most assessors dealing with CUI will get smart about ITAR very quickly; at least in regard to keeping the data within US datacenters and accessible only to US persons*. Assessors may expect documentation specific to ITAR such as the Technology Control Plan (TCP).
* The ITAR regulations actually have a lot of nuance so this summary statement is not completely accurate. For full details about export controlled regulations, reference the Department of State website.
The Defense Federal Acquisition Regulation Supplement (DFARS) 252.204-7012 is another regulation that changes how an organization handles their information systems, which will affect all or almost all companies applying for CMMC Level 3 certification.
Incident handling and CMMC
Expect an assessor to verify you have procedures in place that meet the requirements in Defense Federal Acquisition Regulation Supplement (DFARS) 252.204-7012 for incident reporting and forensics. These procedures would normally be contained in your Incident Response Plan.
DFARS 252.204-7012 and FedRAMP cloud providers
The Defense Federal Acquisition Regulation Supplement (DFARS) 252.204-7012, paragraph D, requires use of FedRAMP authorized cloud providers (or equivalent) for the storage, transmission, or processing of CUI data.
(D) If the Contractor intends to use an external cloud service provider to store, process, or transmit any covered defense information in performance of this contract, the Contractor shall require and ensure that the cloud service provider meets security requirements equivalent to those established by the Government for the Federal Risk and Authorization Management Program (FedRAMP) Moderate baseline (https://www.fedramp.gov/resources/documents/) and that the cloud service provider complies with requirements in paragraphs (c) through (g) of this clause for cyber incident reporting, malicious software, media preservation and protection, access to additional information and equipment necessary for forensic analysis, and cyber incident damage assessment.
DFARS 252.204-7012
This would only be judged against the contractor if they have this clause in their contract (or will have it, for intended future work). During the readiness review for CMMC certification, an assessor should ask if the client has this clause or plans to bid on contracts with the clause.
How is a FedRAMP Moderate baseline verified?
The most straightforward way to tell if a cloud system is FedRAMP moderate is to check the fedramp.gov marketplace. If the cloud solution is listed there, it is at least part way through the authorization process (good enough for most assessors).
Why is FedRAMP a big deal compared to CMMC?
No matter what, if you are using a third party system to handle CUI (meaning it is in-scope for your assessment), you will need to prove that the third party provider is performing at least some CMMC requirements on your behalf. This is called inheriting the practice.
For example, if you have any in-scope systems hosted outside of your facility, you will need to prove that the third party is performing the Physical Protection (PE) requirements in CMMC for those systems. For Infrastructure-as-a-Service (IaaS) clouds not subject to DFARS 252.204.7012 Paragraph D, you would need to prove that the third party is doing less than half of the CMMC Level 3 requirements (somewhere between 10 and 60 of them at a guess). For Software-as-a-Service (SaaS) clouds not subject to DFARS 252.204-7012 Paragraph D, you would need to prove that the third party is doing most of the CMMC Level 3 requirements on the back end (somewhere between 100 and 130 of them at a guess).
In contrast, if we decide that FedRAMP Moderate “or equivalent” applies because the provider is a cloud service provider that stores/processes/transmits CUI, the number of requirements expands greatly. FedRAMP Moderate has 325 requirements.
Proving that your third party provider does 10-130 requirements versus proving that your third party provider does all 325 requirements is a big difference. Both are hard, but one is much harder.
Problem: When does an outsourced system become a cloud system?
Because assessments haven’t started yet, this problem hasn’t emerged as the major issue that it is. Some of the 100,000 – 300,000 defense contractors being assessed will have third party systems in scope that do not meet the requirements in Paragraph D of DFARS 252.204-7012.
Each time assessors find a third party system hosting CUI, they will need to determine if the system is a cloud system and thus requires FedRAMP Moderate or equivalent.
Is every third party system a cloud system? Here are some common scenarios:
- WidgetsUSA is a small business. They hired a Managed Service Provider (MSP) to help them with their server infrastructure. The MSP hosts WidgetsUSA’s servers in their datacenter and manages WidgetsUSA’s information system using a suite of tools running on the MSP’s servers. The MSP purchased all the hardware and software from their vendors and re-sold it with a small markup to WidgetsUSA.
- WidgetsUSA decided to go the enclave route for CMMC Level 3 and purchased an all-in-one enclave solution from ComplianceRUS. WidgetsUSA pays a per-user fee of $4,000 per year per user to ComplianceRUS. ComplianceRUS owns all the back-end servers, software, licensing, and network infrastructure. If WidgetsUSA decided to cancel their contract, ComplianceRUS would retain ownership of all the servers, software, licensing, and network infrastructure.
- WidgetsUSA uses a third party website called www.QualSystems.com to record quality metrics for their work. They upload pictures of each batch of parts made and exact measurements for tensile strength, final dimensions, and any government complaints. The pictures and measurements are CUI.
Are these cloud systems? Do they require FedRAMP Moderate?
Assessors will need to make this decision repeatedly. And honestly, if the question comes up and the assessor decides DFARS 252.204-7012 paragraph D applies, it means that the client will fail their assessment. If the system meets FedRAMP Moderate or equivalent, the client will lead with that information and the question won’t come up.
How to determine if a third party system is a cloud service provider.
The National Institute of Standards and Technology (NIST) published a short paper in 2011 which defines cloud computing.
NIST SP 800-145, The NIST Definition of Cloud Computing
Cloud computing is a model for enabling ubiquitous, convenient, on-demand network access to a shared pool of configurable computing resources (e.g., networks, servers, storage, applications, and services) that can be rapidly provisioned and released with minimal management effort or service provider interaction.
NIST SP 800-145, page 2
The publication defines five Essential Characteristics which define cloud computing.
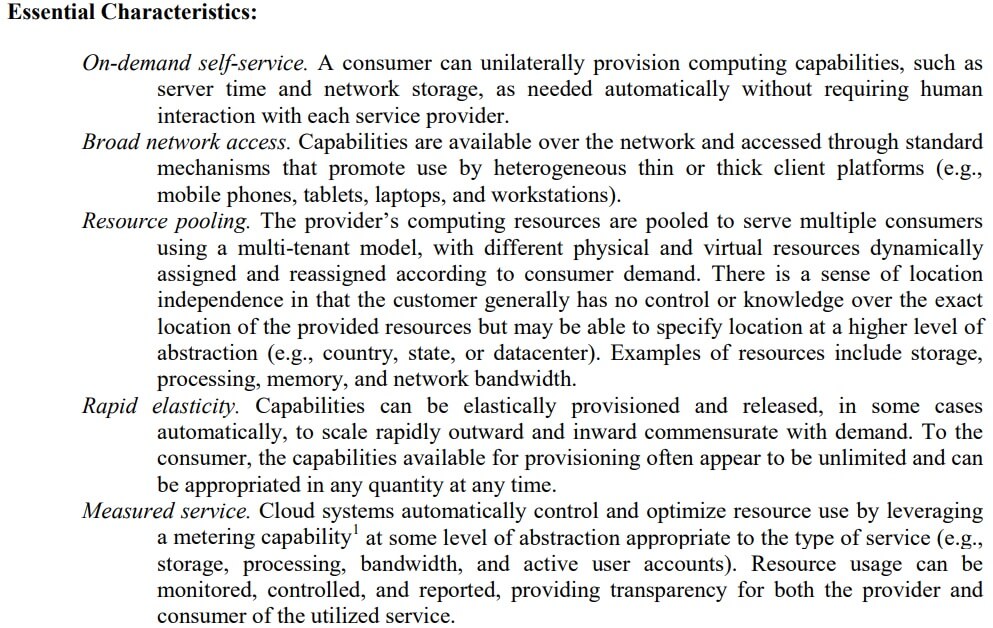
This list of characteristics is actually very narrow. It would make almost all Managed Service Provider infrastructure NOT a cloud. Any custom built systems are NOT a cloud. Having to wait a month while the provider’s staff adds servers for your company would make it NOT a cloud.
Does the Department of Defense agree?
The DFARS Subpart 239.76—CLOUD COMPUTING looks like it agrees with NIST’s definition above.
“Cloud computing” means a model for enabling ubiquitous, convenient, on-demand network access to a shared pool of configurable computing resources (e.g., networks, servers, storage, applications, and services) that can be rapidly provisioned and released with minimal management effort or service provider interaction. This includes other commercial terms, such as on-demand self-service, broad network access, resource pooling, rapid elasticity, and measured service. It also includes commercial offerings for software-as-a-service, infrastructure-as-a-service, and platform-as-a-service.
DFARS Subpart 239.76—CLOUD COMPUTING
Note that the DFARS definition matches the wording from NIST SP 800-145 exactly. This cannot be a mistake. Based on the match, I think it is a safe bet that the DoD will agree with NIST’s essential capabilities of cloud computing as well.
Will the DoD continue to agree that cloud computing is narrowly defined as “on-demand”, “rapidly provisioned and released”, and requires “minimal management effort or service provider interaction”?
If they hold to this definition, Managed Service Providers and most enclave providers should be safe from FedRAMP, as long as they don’t automate their system too much.
Will CMMC assessors verify you are following CUI laws and regulations?
You should expect your CMMC assessor to review your procedures and network design against CUI laws and regulations. Especially DFARS 252.204-7012 compliance and Export Controlled compliance. Make sure to look up the handling requirements for each of your CUI categories and verify that your company is protecting them appropriately!
V. Amira Armond (CISSP, CISA, PMP, MBA) is a computer systems architect, cyber-security consultant, and owner of Kieri Solutions LLC. She specializes in CMMC preparation and DFARS 252.204-7012 compliance, and designing secure and resilient enterprise systems for private sector and the DoD. She is the chief editor for cmmcaudit.org, a public resource for news and informational articles about the Cybersecurity Maturity Model Certification.

Great article, thank you.
If an enclave provider falls under the category of IaaS or PaaS, then it appears that it would fall under the DoD’s definition of cloud computing in DFARS Subpart 239.76. Do you agree?