Continuing the Top 10 Failed Requirements for 800-171! Onward to #7: 3.3.4 “????? ?? ??? ????? ?? ?? ????? ??????? ??????? ???????.”
Sit with me while I tell a story…
?? ???????????? ????????? ???? ???? ???? ???????? ??????? ?????????? ??????? ??? ????? ???? ?? ??? ???? ???.
??3 ???????? ???????? ????? ??? ??????; ???? ????? ??????? ???? ??? ???? ?? ???? ??? ???? ????????. ??? ???? ??? ??????????? ??????? – ????? ??? ?? ???? ???? ??? ???????? ?? ???????.
??? ????????????’? ?????? ?????????????? ????? ???? ???? ??? ?? ???? ?? ??? ????. ?? ??? ????? ??????? ??? ??? ???? ?????? ??? ??? ????, ?? ?? ???? ????? ?? ????? ???. ?????? ???, ???? ???? ?? ????.
And that is how new requirements are born. (sigh)
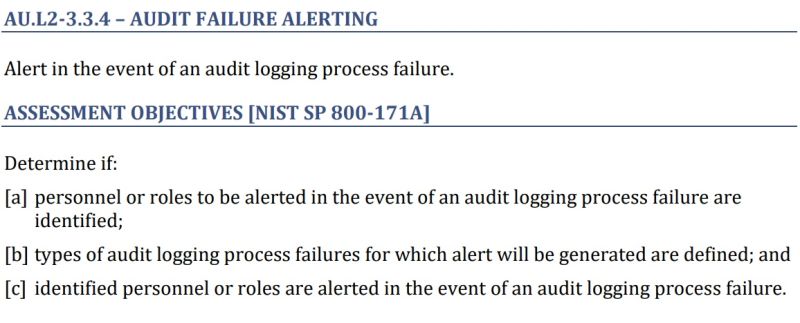
??? 3.3.4, ?? ?????? ?? ???????????? ?? ??? ?? ???? ?????? ????? ?? ?? ??? ??????? ?????? ???? ????? ???? ???? ????? ?? ???????? ?????.
Let’s dissect this.
Push alerts: You can’t go manually check if logs came in. An alert, email, notification, text, ticket, etc, must be generated and sent to a responsible person or team.
Go to the correct people: When being assessed, a great piece of evidence is showing an alert for audit log failure coming in to the person who is identified as responsible for fixing audit log issues.
Drop below an expected level: Assessors understand that some of your systems are 24×7 and some of them are 8×5. For the systems that are 24×7, you should absolutely have individual alerts for each system set up. Think firewalls and servers. For systems that are part-time (laptops), you may need to get inventive. For both situations, you should identify thresholds for what is “normal” log generation.
For example, you could create a logic rule: your firewall should generate at least 10,000 events per day. If it drops below that level, send an alert to the security team.
Inheritance: This requirement is hard to prove with cloud systems, particularly SaaS clouds. We know there are servers and firewalls and networking equipment in the cloud but they aren’t visible to you as the customer. You need to verify that the cloud admins are performing this requirement in-house. This is where FedRAMP is useful – FedRAMP moderate baseline includes this requirement (so if a cloud is FedRAMP authorized, they are doing this internally). If you store, process, or transmit CUI in an SaaS cloud, you should discuss how you verified that the cloud is performing 3.3.4.