Continuing the Top 10 “Other than Satisfied Requirements” for 800-171 assessments by DIBCAC. “????????, ??????, ??? ??????? ??????????? ??? ??????????? ?????? ????? ?? ? ?????? ??????.” This is the third most “Other than Satisfied” requirement.
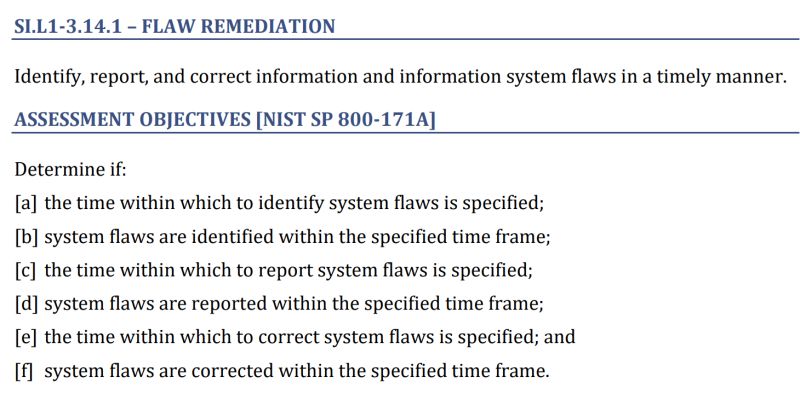
3.14.1 is both misunderstood and very hard to implement. Both problems cause failures.
??? ?? 3.14.1 ??????????????
Most people read the requirement as just the last assessment objective: [?] ?????? ????? ??? ????????? ?????? ??? ????????? ???? ?????.
However, other objectives require you to specify timeframes for identifying flaws and reporting flaws, then show proof of identifying and reporting.
These assessment objectives assume you have separate people doing tasks that most small IT departments assign to a single person. This is why they break out identifying from reporting, reporting from patching. Because when you’ve got millions of dollars of IT budget (Hello U.S. Government), those tasks are done by different departments.
When a single person is in charge from start-to-finish, they may have trouble showing evidence that they “reported” the flaws to themselves. I’m rolling my eyes right now as I write this, but seriously, a common solution is adding a reporting step to your process to document what patches are needed before you start patching. The list of flaws is never reviewed by anyone else, except as evidence you are reporting on schedule. Whoopee.
??? ?? 3.14.1 ???? ?? ??????????
Patching systems is one of the most costly requirements in 800-171 (in terms of labor).
Patching a core system causes brief downtime and can cause it to crash, causing lots of downtime for lots of people. In most companies, you are paying for an IT person to monitor important systems during the entire patch, reboot, and function check process.
As systems get older, vendors start asking for extra money if you want eligibility for continued patches.
Ironically, our role models, the US Government, often struggle with patching on schedule, even though they have more IT resources. It is common to see them take 3-6 months to deploy after a flaw has been ‘identified’.
What to do if you have a system that cannot be patched because it breaks, and you can’t get an alternate system? This is a good candidate for an enduring exception to policy and/or a multi-year POA&M. (Talk to a cybersecurity professional to plan this out, because it can burn you if done wrong.)
Shameless plug: The Kieri Compliance Documentation includes customizable timeframes for identifying, reporting, and patching. We include steps in our process to document what patches are needed (??????????? and ?????????) so that you don’t fail because of a silly misunderstanding.